
.- - -----÷M÷E÷N÷U÷------------------------------------------------------------- --- ---- -------------.
! WALL ! STATS ! GOODIES ! YARA ! FAQ ! RSS ! EMV !
`-------------- - --- ---------- -------- -------- -------- -------- ----------------- - ---- ---- --'
ATM MALWARE NOTICE
7fac4b739c412b074ee13e181c0900a350b4df9499515febb75008e6955b9674
Date...........: 2017-04-12
Family.........: ATMii
File name......: exe.exe
File size......: 8.50 KB
Type file......: EXE/Windows
Virscan........: VT - HA
Documentation..: https://securelist.com/atmii-a-small-but-effective-atm-robber/82707/
Entropy:
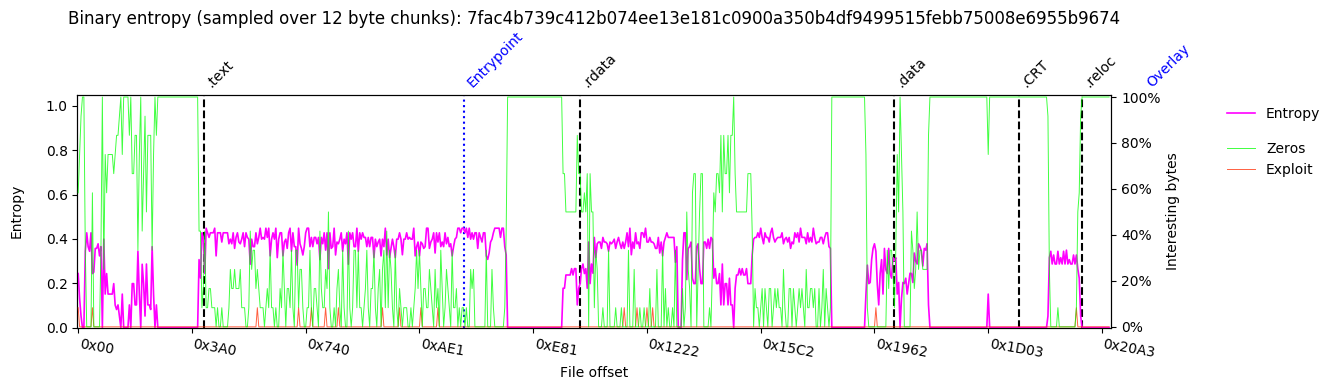 Binary Histogram:
Binary Histogram:
 === PEDUMP REPORT ===
=== PEDUMP REPORT ===
=== MZ Header ===
signature: "MZ"
bytes_in_last_block: 144 0x90
blocks_in_file: 3 3
num_relocs: 0 0
header_paragraphs: 4 4
min_extra_paragraphs: 0 0
max_extra_paragraphs: 65535 0xffff
ss: 0 0
sp: 184 0xb8
checksum: 0 0
ip: 0 0
cs: 0 0
reloc_table_offset: 64 0x40
overlay_number: 0 0
reserved0: 0 0
oem_id: 0 0
oem_info: 0 0
reserved2: 0 0
reserved3: 0 0
reserved4: 0 0
reserved5: 0 0
reserved6: 0 0
lfanew: 216 0xd8
=== DOS STUB ===
00000000: 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th|
00000010: 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|
00000020: 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |
00000030: 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|
=== RICH Header ===
LIB_ID VERSION TIMES_USED
158 9e 40219 9d1b 1 1
170 aa 40219 9d1b 2 2
147 93 30729 7809 11 b
1 1 0 0 34 22
175 af 40219 9d1b 3 3
157 9d 40219 9d1b 1 1
=== PE Header ===
signature: "PE\x00\x00"
# IMAGE_FILE_HEADER:
Machine: 332 0x14c x86
NumberOfSections: 5 5
TimeDateStamp: "2013-11-01 14:33:23"
PointerToSymbolTable: 0 0
NumberOfSymbols: 0 0
SizeOfOptionalHeader: 224 0xe0
Characteristics: 258 0x102 EXECUTABLE_IMAGE, 32BIT_MACHINE
# IMAGE_OPTIONAL_HEADER32:
Magic: 267 0x10b 32-bit executable
LinkerVersion: 10.0
SizeOfCode: 3072 0xc00
SizeOfInitializedData: 4608 0x1200
SizeOfUninitializedData: 0 0
AddressOfEntryPoint: 6224 0x1850
BaseOfCode: 4096 0x1000
BaseOfData: 8192 0x2000
ImageBase: 4194304 0x400000
SectionAlignment: 4096 0x1000
FileAlignment: 512 0x200
OperatingSystemVersion: 5.1
ImageVersion: 0.0
SubsystemVersion: 5.1
Reserved1: 0 0
SizeOfImage: 24576 0x6000
SizeOfHeaders: 1024 0x400
CheckSum: 0 0
Subsystem: 2 2 WINDOWS_GUI
DllCharacteristics: 34112 0x8540 DYNAMIC_BASE, NX_COMPAT, NO_SEH
TERMINAL_SERVER_AWARE
SizeOfStackReserve: 1048576 0x100000
SizeOfStackCommit: 4096 0x1000
SizeOfHeapReserve: 1048576 0x100000
SizeOfHeapCommit: 4096 0x1000
LoaderFlags: 0 0
NumberOfRvaAndSizes: 16 0x10
=== DATA DIRECTORY ===
EXPORT rva:0x 0 size:0x 0
IMPORT rva:0x 2530 size:0x 78
RESOURCE rva:0x 0 size:0x 0
EXCEPTION rva:0x 0 size:0x 0
SECURITY rva:0x 0 size:0x 0
BASERELOC rva:0x 5000 size:0x 110
DEBUG rva:0x 0 size:0x 0
ARCHITECTURE rva:0x 0 size:0x 0
GLOBALPTR rva:0x 0 size:0x 0
TLS rva:0x 0 size:0x 0
LOAD_CONFIG rva:0x 0 size:0x 0
Bound_IAT rva:0x 0 size:0x 0
IAT rva:0x 2000 size:0x 94
Delay_IAT rva:0x 0 size:0x 0
CLR_Header rva:0x 0 size:0x 0
rva:0x 0 size:0x 0
=== SECTIONS ===
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
.text 1000 a24 c00 400 0 0 0 0 60000020 R-X CODE
.rdata 2000 8d8 a00 1000 0 0 0 0 40000040 R-- IDATA
.data 3000 214 400 1a00 0 0 0 0 c0000040 RW- IDATA
.CRT 4000 4 200 1e00 0 0 0 0 40000040 R-- IDATA
.reloc 5000 162 200 2000 0 0 0 0 42000040 R-- IDATA DISCARDABLE
=== IMPORTS ===
MODULE_NAME HINT ORD FUNCTION_NAME
SHLWAPI.dll 30 PathAddBackslashW
SHLWAPI.dll 8b PathRemoveFileSpecW
KERNEL32.dll 4ed VirtualFreeEx
KERNEL32.dll 4ea VirtualAllocEx
KERNEL32.dll 52e WriteProcessMemory
KERNEL32.dll 187 GetCommandLineW
KERNEL32.dll 466 SetFilePointer
KERNEL32.dll 54d lstrlenA
KERNEL32.dll 4f9 WaitForSingleObject
KERNEL32.dll 218 GetModuleHandleW
KERNEL32.dll a9 CreateRemoteThread
KERNEL32.dll 525 WriteFile
KERNEL32.dll 380 OpenProcess
KERNEL32.dll 214 GetModuleFileNameW
KERNEL32.dll 8f CreateFileW
KERNEL32.dll 52b WritePrivateProfileStringW
KERNEL32.dll 304 IsProcessorFeaturePresent
KERNEL32.dll 245 GetProcAddress
KERNEL32.dll 396 Process32FirstW
KERNEL32.dll 1e0 GetExitCodeThread
KERNEL32.dll 398 Process32NextW
KERNEL32.dll 545 lstrcmpiW
KERNEL32.dll 53f lstrcatW
KERNEL32.dll be CreateToolhelp32Snapshot
KERNEL32.dll 52 CloseHandle
KERNEL32.dll 348 LocalFree
KERNEL32.dll 548 lstrcpyW
KERNEL32.dll 202 GetLastError
USER32.dll 332 wsprintfA
ADVAPI32.dll 2b6 SetSecurityDescriptorDacl
ADVAPI32.dll 177 InitializeSecurityDescriptor
SHELL32.dll 6 CommandLineToArgvW
File pos Mem pos ID Text
======== ======= == ====
00000000004D 00000040004D 0 !This program cannot be run in DOS mode.
0000000000BF 0000004000BF 0 .Rich
0000000001D0 0000004001D0 0 .text
0000000001F8 0000004001F8 0 .rdata
00000000021F 00000040021F 0 @.data
00000000026F 00000040026F 0 @.reloc
000000000980 000000401580 0 Whh#@
000000000A74 000000401674 0 Phh#@
000000000B3A 00000040173A 0 Wh $@
000000000B70 000000401770 0 RhD$@
000000000B94 000000401794 0 |Wh $@
000000000BC5 0000004017C5 0 Ph|$@
000000000BF0 0000004017F0 0 Rh $@
0000000010D4 0000004020D4 0 LoadLibraryW
000000001100 000000402100 0 FreeLibrary
00000000110C 00000040210C 0 GetLastError
00000000111C 00000040211C 0 InjectDll
000000001128 000000402128 0 (%d):%s() Failed to write shellcode to process
000000001158 000000402158 0 (%d):%s() Failed to write params to process
000000001188 000000402188 0 (%d):%s() InitializeSecurityDescriptor - failed %d
0000000011BC 0000004021BC 0 (%d):%s() SetSecurityDescriptorDacl() error %d
0000000011EC 0000004021EC 0 (%d):%s() Remote thread created, waiting unloadevent signal
00000000122C 00000040222C 0 (%d):%s() Failed to get exit code thread
000000001258 000000402258 0 (%d):%s() Thread job done, exit code thread %d
000000001288 000000402288 0 (%d):%s() Try unload library/shellcode
0000000012B0 0000004022B0 0 (%d):%s() Thread created, waiting for thread exit
0000000012E4 0000004022E4 0 (%d):%s() Done, unload library thread exit code = %d
00000000131C 00000040231C 0 (%d):%s() Release remote process memory
000000001348 000000402348 0 (%d):%s() Open process failed
000000001368 000000402368 0 SearchAndInject
000000001378 000000402378 0 (%d):%s() CreateToolhelp32Snapshot
00000000139C 00000040239C 0 (%d):%s() Parsing processes
0000000013BC 0000004023BC 0 (%d):%s() -------------------------------------------
0000000013F4 0000004023F4 0 (%d):%s() Process found %S
000000001420 000000402420 0 TriggerCmd
00000000142C 00000040242C 0 (%d):%s() cmd created
000000001464 000000402464 0 (%d):%s() data wrote
0000000014A0 0000004024A0 0 (%d):%s() failed to write parameters iNumArgs = %d
0000000014D4 0000004024D4 0 (%d):%s() Invalid num args
00000000163E 00000040263E 0 PathRemoveFileSpecW
000000001654 000000402654 0 PathAddBackslashW
000000001666 000000402666 0 SHLWAPI.dll
000000001674 000000402674 0 VirtualFreeEx
000000001684 000000402684 0 VirtualAllocEx
000000001696 000000402696 0 WriteProcessMemory
0000000016AC 0000004026AC 0 GetCommandLineW
0000000016BE 0000004026BE 0 SetFilePointer
0000000016D0 0000004026D0 0 lstrlenA
0000000016DC 0000004026DC 0 WaitForSingleObject
0000000016F2 0000004026F2 0 GetModuleHandleW
000000001706 000000402706 0 CreateRemoteThread
00000000171C 00000040271C 0 WriteFile
000000001728 000000402728 0 OpenProcess
000000001736 000000402736 0 GetModuleFileNameW
00000000174C 00000040274C 0 CreateFileW
00000000175A 00000040275A 0 WritePrivateProfileStringW
000000001778 000000402778 0 GetLastError
000000001788 000000402788 0 GetProcAddress
00000000179A 00000040279A 0 Process32FirstW
0000000017AC 0000004027AC 0 GetExitCodeThread
File pos Mem pos ID Text
======== ======= == ====
0000000017C0 0000004027C0 0 Process32NextW
0000000017D2 0000004027D2 0 lstrcmpiW
0000000017DE 0000004027DE 0 lstrcatW
0000000017EA 0000004027EA 0 CreateToolhelp32Snapshot
000000001806 000000402806 0 CloseHandle
000000001814 000000402814 0 LocalFree
000000001820 000000402820 0 lstrcpyW
00000000182A 00000040282A 0 KERNEL32.dll
00000000183A 00000040283A 0 wsprintfA
000000001844 000000402844 0 USER32.dll
000000001852 000000402852 0 InitializeSecurityDescriptor
000000001872 000000402872 0 SetSecurityDescriptorDacl
00000000188C 00000040288C 0 ADVAPI32.dll
00000000189C 00000040289C 0 CommandLineToArgvW
0000000018B0 0000004028B0 0 SHELL32.dll
0000000018BE 0000004028BE 0 IsProcessorFeaturePresent
000000001A56 000000403056 0 YYYYY
000000001A62 000000403062 0 YYYYYYYYYYYY
000000001A70 000000403070 0 }YPPPPYYYYa
000000001A86 000000403086 0 YYYYYYYYYYY
000000001B38 000000403138 0 JJJJKRJJJJOLJJJJJJJJUE@JJJEYMFJ]JJJJJJJJJJJJJJacgNJJkmJJEmJJDEJJ
00000000200B 00000040500B 0 0;0B0[0k0z0
000000002019 000000405019 0 1C1K1P1X1
000000002023 000000405023 0 1e1u1z1
000000002037 000000405037 0 2-2L2U2e2l2
000000002055 000000405055 0 3F3V3f3
00000000206B 00000040506B 0 434C4S4q4
000000002085 000000405085 0 535?5O5V5|5
00000000209D 00000040509D 0 6#616>6K6[6v6
0000000020B5 0000004050B5 0 767<7L7d7l7r7w7
0000000020DD 0000004050DD 0 8/868b8i8y8~8
000000001094 000000402094 0 C:\ATM\tlogsr.log
0000000010B8 0000004020B8 0 C:\ATM\c.ini
0000000010E4 0000004020E4 0 kernel32.dll
000000001410 000000402410 0 dll.dll
00000000147C 00000040247C 0 currency
000000001490 000000402490 0 amount
0000000014F0 0000004024F0 0 /load
0000000014FC 0000004024FC 0 atmapp.exe
000000001520 000000402520 0 /unload
00000000004D 00000040004D 0 !This program cannot be run in DOS mode.
0000000000BF 0000004000BF 0 .Rich
0000000001D0 0000004001D0 0 .text
0000000001F8 0000004001F8 0 .rdata
00000000021F 00000040021F 0 @.data
00000000026F 00000040026F 0 @.reloc
000000000980 000000401580 0 Whh#@
000000000A74 000000401674 0 Phh#@
000000000B3A 00000040173A 0 Wh $@
000000000B70 000000401770 0 RhD$@
000000000B94 000000401794 0 |Wh $@
000000000BC5 0000004017C5 0 Ph|$@
000000000BF0 0000004017F0 0 Rh $@
0000000010D4 0000004020D4 0 LoadLibraryW
000000001100 000000402100 0 FreeLibrary
00000000110C 00000040210C 0 GetLastError
00000000111C 00000040211C 0 InjectDll
000000001128 000000402128 0 (%d):%s() Failed to write shellcode to process
000000001158 000000402158 0 (%d):%s() Failed to write params to process
000000001188 000000402188 0 (%d):%s() InitializeSecurityDescriptor - failed %d
File pos Mem pos ID Text
======== ======= == ====
0000000011BC 0000004021BC 0 (%d):%s() SetSecurityDescriptorDacl() error %d
0000000011EC 0000004021EC 0 (%d):%s() Remote thread created, waiting unloadevent signal
00000000122C 00000040222C 0 (%d):%s() Failed to get exit code thread
000000001258 000000402258 0 (%d):%s() Thread job done, exit code thread %d
000000001288 000000402288 0 (%d):%s() Try unload library/shellcode
0000000012B0 0000004022B0 0 (%d):%s() Thread created, waiting for thread exit
0000000012E4 0000004022E4 0 (%d):%s() Done, unload library thread exit code = %d
00000000131C 00000040231C 0 (%d):%s() Release remote process memory
000000001348 000000402348 0 (%d):%s() Open process failed
000000001368 000000402368 0 SearchAndInject
000000001378 000000402378 0 (%d):%s() CreateToolhelp32Snapshot
00000000139C 00000040239C 0 (%d):%s() Parsing processes
0000000013BC 0000004023BC 0 (%d):%s() -------------------------------------------
0000000013F4 0000004023F4 0 (%d):%s() Process found %S
000000001420 000000402420 0 TriggerCmd
00000000142C 00000040242C 0 (%d):%s() cmd created
000000001464 000000402464 0 (%d):%s() data wrote
0000000014A0 0000004024A0 0 (%d):%s() failed to write parameters iNumArgs = %d
0000000014D4 0000004024D4 0 (%d):%s() Invalid num args
00000000163E 00000040263E 0 PathRemoveFileSpecW
000000001654 000000402654 0 PathAddBackslashW
000000001666 000000402666 0 SHLWAPI.dll
000000001674 000000402674 0 VirtualFreeEx
000000001684 000000402684 0 VirtualAllocEx
000000001696 000000402696 0 WriteProcessMemory
0000000016AC 0000004026AC 0 GetCommandLineW
0000000016BE 0000004026BE 0 SetFilePointer
0000000016D0 0000004026D0 0 lstrlenA
0000000016DC 0000004026DC 0 WaitForSingleObject
0000000016F2 0000004026F2 0 GetModuleHandleW
000000001706 000000402706 0 CreateRemoteThread
00000000171C 00000040271C 0 WriteFile
000000001728 000000402728 0 OpenProcess
000000001736 000000402736 0 GetModuleFileNameW
00000000174C 00000040274C 0 CreateFileW
00000000175A 00000040275A 0 WritePrivateProfileStringW
000000001778 000000402778 0 GetLastError
000000001788 000000402788 0 GetProcAddress
00000000179A 00000040279A 0 Process32FirstW
0000000017AC 0000004027AC 0 GetExitCodeThread
0000000017C0 0000004027C0 0 Process32NextW
0000000017D2 0000004027D2 0 lstrcmpiW
0000000017DE 0000004027DE 0 lstrcatW
0000000017EA 0000004027EA 0 CreateToolhelp32Snapshot
000000001806 000000402806 0 CloseHandle
000000001814 000000402814 0 LocalFree
000000001820 000000402820 0 lstrcpyW
00000000182A 00000040282A 0 KERNEL32.dll
00000000183A 00000040283A 0 wsprintfA
000000001844 000000402844 0 USER32.dll
000000001852 000000402852 0 InitializeSecurityDescriptor
000000001872 000000402872 0 SetSecurityDescriptorDacl
00000000188C 00000040288C 0 ADVAPI32.dll
00000000189C 00000040289C 0 CommandLineToArgvW
0000000018B0 0000004028B0 0 SHELL32.dll
0000000018BE 0000004028BE 0 IsProcessorFeaturePresent
000000001A56 000000403056 0 YYYYY
000000001A62 000000403062 0 YYYYYYYYYYYY
000000001A70 000000403070 0 }YPPPPYYYYa
000000001A86 000000403086 0 YYYYYYYYYYY
File pos Mem pos ID Text
======== ======= == ====
000000001B38 000000403138 0 JJJJKRJJJJOLJJJJJJJJUE@JJJEYMFJ]JJJJJJJJJJJJJJacgNJJkmJJEmJJDEJJ
00000000200B 00000040500B 0 0;0B0[0k0z0
000000002019 000000405019 0 1C1K1P1X1
000000002023 000000405023 0 1e1u1z1
000000002037 000000405037 0 2-2L2U2e2l2
000000002055 000000405055 0 3F3V3f3
00000000206B 00000040506B 0 434C4S4q4
000000002085 000000405085 0 535?5O5V5|5
00000000209D 00000040509D 0 6#616>6K6[6v6
0000000020B5 0000004050B5 0 767<7L7d7l7r7w7
0000000020DD 0000004050DD 0 8/868b8i8y8~8
000000001094 000000402094 0 C:\ATM\tlogsr.log
0000000010B8 0000004020B8 0 C:\ATM\c.ini
0000000010E4 0000004020E4 0 kernel32.dll
000000001410 000000402410 0 dll.dll
00000000147C 00000040247C 0 currency
000000001490 000000402490 0 amount
0000000014F0 0000004024F0 0 /load
0000000014FC 0000004024FC 0 atmapp.exe
000000001520 000000402520 0 /unload

 Binary Histogram:
Binary Histogram:
 === PEDUMP REPORT ===
=== MZ Header ===
signature: "MZ"
bytes_in_last_block: 144 0x90
blocks_in_file: 3 3
num_relocs: 0 0
header_paragraphs: 4 4
min_extra_paragraphs: 0 0
max_extra_paragraphs: 65535 0xffff
ss: 0 0
sp: 184 0xb8
checksum: 0 0
ip: 0 0
cs: 0 0
reloc_table_offset: 64 0x40
overlay_number: 0 0
reserved0: 0 0
oem_id: 0 0
oem_info: 0 0
reserved2: 0 0
reserved3: 0 0
reserved4: 0 0
reserved5: 0 0
reserved6: 0 0
lfanew: 216 0xd8
=== DOS STUB ===
00000000: 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th|
00000010: 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|
00000020: 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |
00000030: 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|
=== RICH Header ===
LIB_ID VERSION TIMES_USED
158 9e 40219 9d1b 1 1
170 aa 40219 9d1b 2 2
147 93 30729 7809 11 b
1 1 0 0 34 22
175 af 40219 9d1b 3 3
157 9d 40219 9d1b 1 1
=== PE Header ===
signature: "PE\x00\x00"
# IMAGE_FILE_HEADER:
Machine: 332 0x14c x86
NumberOfSections: 5 5
TimeDateStamp: "2013-11-01 14:33:23"
PointerToSymbolTable: 0 0
NumberOfSymbols: 0 0
SizeOfOptionalHeader: 224 0xe0
Characteristics: 258 0x102 EXECUTABLE_IMAGE, 32BIT_MACHINE
# IMAGE_OPTIONAL_HEADER32:
Magic: 267 0x10b 32-bit executable
LinkerVersion: 10.0
SizeOfCode: 3072 0xc00
SizeOfInitializedData: 4608 0x1200
SizeOfUninitializedData: 0 0
AddressOfEntryPoint: 6224 0x1850
BaseOfCode: 4096 0x1000
BaseOfData: 8192 0x2000
ImageBase: 4194304 0x400000
SectionAlignment: 4096 0x1000
FileAlignment: 512 0x200
OperatingSystemVersion: 5.1
ImageVersion: 0.0
SubsystemVersion: 5.1
Reserved1: 0 0
SizeOfImage: 24576 0x6000
SizeOfHeaders: 1024 0x400
CheckSum: 0 0
Subsystem: 2 2 WINDOWS_GUI
DllCharacteristics: 34112 0x8540 DYNAMIC_BASE, NX_COMPAT, NO_SEH
TERMINAL_SERVER_AWARE
SizeOfStackReserve: 1048576 0x100000
SizeOfStackCommit: 4096 0x1000
SizeOfHeapReserve: 1048576 0x100000
SizeOfHeapCommit: 4096 0x1000
LoaderFlags: 0 0
NumberOfRvaAndSizes: 16 0x10
=== DATA DIRECTORY ===
EXPORT rva:0x 0 size:0x 0
IMPORT rva:0x 2530 size:0x 78
RESOURCE rva:0x 0 size:0x 0
EXCEPTION rva:0x 0 size:0x 0
SECURITY rva:0x 0 size:0x 0
BASERELOC rva:0x 5000 size:0x 110
DEBUG rva:0x 0 size:0x 0
ARCHITECTURE rva:0x 0 size:0x 0
GLOBALPTR rva:0x 0 size:0x 0
TLS rva:0x 0 size:0x 0
LOAD_CONFIG rva:0x 0 size:0x 0
Bound_IAT rva:0x 0 size:0x 0
IAT rva:0x 2000 size:0x 94
Delay_IAT rva:0x 0 size:0x 0
CLR_Header rva:0x 0 size:0x 0
rva:0x 0 size:0x 0
=== SECTIONS ===
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
.text 1000 a24 c00 400 0 0 0 0 60000020 R-X CODE
.rdata 2000 8d8 a00 1000 0 0 0 0 40000040 R-- IDATA
.data 3000 214 400 1a00 0 0 0 0 c0000040 RW- IDATA
.CRT 4000 4 200 1e00 0 0 0 0 40000040 R-- IDATA
.reloc 5000 162 200 2000 0 0 0 0 42000040 R-- IDATA DISCARDABLE
=== IMPORTS ===
MODULE_NAME HINT ORD FUNCTION_NAME
SHLWAPI.dll 30 PathAddBackslashW
SHLWAPI.dll 8b PathRemoveFileSpecW
KERNEL32.dll 4ed VirtualFreeEx
KERNEL32.dll 4ea VirtualAllocEx
KERNEL32.dll 52e WriteProcessMemory
KERNEL32.dll 187 GetCommandLineW
KERNEL32.dll 466 SetFilePointer
KERNEL32.dll 54d lstrlenA
KERNEL32.dll 4f9 WaitForSingleObject
KERNEL32.dll 218 GetModuleHandleW
KERNEL32.dll a9 CreateRemoteThread
KERNEL32.dll 525 WriteFile
KERNEL32.dll 380 OpenProcess
KERNEL32.dll 214 GetModuleFileNameW
KERNEL32.dll 8f CreateFileW
KERNEL32.dll 52b WritePrivateProfileStringW
KERNEL32.dll 304 IsProcessorFeaturePresent
KERNEL32.dll 245 GetProcAddress
KERNEL32.dll 396 Process32FirstW
KERNEL32.dll 1e0 GetExitCodeThread
KERNEL32.dll 398 Process32NextW
KERNEL32.dll 545 lstrcmpiW
KERNEL32.dll 53f lstrcatW
KERNEL32.dll be CreateToolhelp32Snapshot
KERNEL32.dll 52 CloseHandle
KERNEL32.dll 348 LocalFree
KERNEL32.dll 548 lstrcpyW
KERNEL32.dll 202 GetLastError
USER32.dll 332 wsprintfA
ADVAPI32.dll 2b6 SetSecurityDescriptorDacl
ADVAPI32.dll 177 InitializeSecurityDescriptor
SHELL32.dll 6 CommandLineToArgvW
=== Strings ===
File pos Mem pos ID Text
======== ======= == ====
00000000004D 00000040004D 0 !This program cannot be run in DOS mode.
0000000000BF 0000004000BF 0 .Rich
0000000001D0 0000004001D0 0 .text
0000000001F8 0000004001F8 0 .rdata
00000000021F 00000040021F 0 @.data
00000000026F 00000040026F 0 @.reloc
000000000980 000000401580 0 Whh#@
000000000A74 000000401674 0 Phh#@
000000000B3A 00000040173A 0 Wh $@
000000000B70 000000401770 0 RhD$@
000000000B94 000000401794 0 |Wh $@
000000000BC5 0000004017C5 0 Ph|$@
000000000BF0 0000004017F0 0 Rh $@
0000000010D4 0000004020D4 0 LoadLibraryW
000000001100 000000402100 0 FreeLibrary
00000000110C 00000040210C 0 GetLastError
00000000111C 00000040211C 0 InjectDll
000000001128 000000402128 0 (%d):%s() Failed to write shellcode to process
000000001158 000000402158 0 (%d):%s() Failed to write params to process
000000001188 000000402188 0 (%d):%s() InitializeSecurityDescriptor - failed %d
0000000011BC 0000004021BC 0 (%d):%s() SetSecurityDescriptorDacl() error %d
0000000011EC 0000004021EC 0 (%d):%s() Remote thread created, waiting unloadevent signal
00000000122C 00000040222C 0 (%d):%s() Failed to get exit code thread
000000001258 000000402258 0 (%d):%s() Thread job done, exit code thread %d
000000001288 000000402288 0 (%d):%s() Try unload library/shellcode
0000000012B0 0000004022B0 0 (%d):%s() Thread created, waiting for thread exit
0000000012E4 0000004022E4 0 (%d):%s() Done, unload library thread exit code = %d
00000000131C 00000040231C 0 (%d):%s() Release remote process memory
000000001348 000000402348 0 (%d):%s() Open process failed
000000001368 000000402368 0 SearchAndInject
000000001378 000000402378 0 (%d):%s() CreateToolhelp32Snapshot
00000000139C 00000040239C 0 (%d):%s() Parsing processes
0000000013BC 0000004023BC 0 (%d):%s() -------------------------------------------
0000000013F4 0000004023F4 0 (%d):%s() Process found %S
000000001420 000000402420 0 TriggerCmd
00000000142C 00000040242C 0 (%d):%s() cmd created
000000001464 000000402464 0 (%d):%s() data wrote
0000000014A0 0000004024A0 0 (%d):%s() failed to write parameters iNumArgs = %d
0000000014D4 0000004024D4 0 (%d):%s() Invalid num args
00000000163E 00000040263E 0 PathRemoveFileSpecW
000000001654 000000402654 0 PathAddBackslashW
000000001666 000000402666 0 SHLWAPI.dll
000000001674 000000402674 0 VirtualFreeEx
000000001684 000000402684 0 VirtualAllocEx
000000001696 000000402696 0 WriteProcessMemory
0000000016AC 0000004026AC 0 GetCommandLineW
0000000016BE 0000004026BE 0 SetFilePointer
0000000016D0 0000004026D0 0 lstrlenA
0000000016DC 0000004026DC 0 WaitForSingleObject
0000000016F2 0000004026F2 0 GetModuleHandleW
000000001706 000000402706 0 CreateRemoteThread
00000000171C 00000040271C 0 WriteFile
000000001728 000000402728 0 OpenProcess
000000001736 000000402736 0 GetModuleFileNameW
00000000174C 00000040274C 0 CreateFileW
00000000175A 00000040275A 0 WritePrivateProfileStringW
000000001778 000000402778 0 GetLastError
000000001788 000000402788 0 GetProcAddress
00000000179A 00000040279A 0 Process32FirstW
0000000017AC 0000004027AC 0 GetExitCodeThread
File pos Mem pos ID Text
======== ======= == ====
0000000017C0 0000004027C0 0 Process32NextW
0000000017D2 0000004027D2 0 lstrcmpiW
0000000017DE 0000004027DE 0 lstrcatW
0000000017EA 0000004027EA 0 CreateToolhelp32Snapshot
000000001806 000000402806 0 CloseHandle
000000001814 000000402814 0 LocalFree
000000001820 000000402820 0 lstrcpyW
00000000182A 00000040282A 0 KERNEL32.dll
00000000183A 00000040283A 0 wsprintfA
000000001844 000000402844 0 USER32.dll
000000001852 000000402852 0 InitializeSecurityDescriptor
000000001872 000000402872 0 SetSecurityDescriptorDacl
00000000188C 00000040288C 0 ADVAPI32.dll
00000000189C 00000040289C 0 CommandLineToArgvW
0000000018B0 0000004028B0 0 SHELL32.dll
0000000018BE 0000004028BE 0 IsProcessorFeaturePresent
000000001A56 000000403056 0 YYYYY
000000001A62 000000403062 0 YYYYYYYYYYYY
000000001A70 000000403070 0 }YPPPPYYYYa
000000001A86 000000403086 0 YYYYYYYYYYY
000000001B38 000000403138 0 JJJJKRJJJJOLJJJJJJJJUE@JJJEYMFJ]JJJJJJJJJJJJJJacgNJJkmJJEmJJDEJJ
00000000200B 00000040500B 0 0;0B0[0k0z0
000000002019 000000405019 0 1C1K1P1X1
000000002023 000000405023 0 1e1u1z1
000000002037 000000405037 0 2-2L2U2e2l2
000000002055 000000405055 0 3F3V3f3
00000000206B 00000040506B 0 434C4S4q4
000000002085 000000405085 0 535?5O5V5|5
00000000209D 00000040509D 0 6#616>6K6[6v6
0000000020B5 0000004050B5 0 767<7L7d7l7r7w7
0000000020DD 0000004050DD 0 8/868b8i8y8~8
000000001094 000000402094 0 C:\ATM\tlogsr.log
0000000010B8 0000004020B8 0 C:\ATM\c.ini
0000000010E4 0000004020E4 0 kernel32.dll
000000001410 000000402410 0 dll.dll
00000000147C 00000040247C 0 currency
000000001490 000000402490 0 amount
0000000014F0 0000004024F0 0 /load
0000000014FC 0000004024FC 0 atmapp.exe
000000001520 000000402520 0 /unload
00000000004D 00000040004D 0 !This program cannot be run in DOS mode.
0000000000BF 0000004000BF 0 .Rich
0000000001D0 0000004001D0 0 .text
0000000001F8 0000004001F8 0 .rdata
00000000021F 00000040021F 0 @.data
00000000026F 00000040026F 0 @.reloc
000000000980 000000401580 0 Whh#@
000000000A74 000000401674 0 Phh#@
000000000B3A 00000040173A 0 Wh $@
000000000B70 000000401770 0 RhD$@
000000000B94 000000401794 0 |Wh $@
000000000BC5 0000004017C5 0 Ph|$@
000000000BF0 0000004017F0 0 Rh $@
0000000010D4 0000004020D4 0 LoadLibraryW
000000001100 000000402100 0 FreeLibrary
00000000110C 00000040210C 0 GetLastError
00000000111C 00000040211C 0 InjectDll
000000001128 000000402128 0 (%d):%s() Failed to write shellcode to process
000000001158 000000402158 0 (%d):%s() Failed to write params to process
000000001188 000000402188 0 (%d):%s() InitializeSecurityDescriptor - failed %d
File pos Mem pos ID Text
======== ======= == ====
0000000011BC 0000004021BC 0 (%d):%s() SetSecurityDescriptorDacl() error %d
0000000011EC 0000004021EC 0 (%d):%s() Remote thread created, waiting unloadevent signal
00000000122C 00000040222C 0 (%d):%s() Failed to get exit code thread
000000001258 000000402258 0 (%d):%s() Thread job done, exit code thread %d
000000001288 000000402288 0 (%d):%s() Try unload library/shellcode
0000000012B0 0000004022B0 0 (%d):%s() Thread created, waiting for thread exit
0000000012E4 0000004022E4 0 (%d):%s() Done, unload library thread exit code = %d
00000000131C 00000040231C 0 (%d):%s() Release remote process memory
000000001348 000000402348 0 (%d):%s() Open process failed
000000001368 000000402368 0 SearchAndInject
000000001378 000000402378 0 (%d):%s() CreateToolhelp32Snapshot
00000000139C 00000040239C 0 (%d):%s() Parsing processes
0000000013BC 0000004023BC 0 (%d):%s() -------------------------------------------
0000000013F4 0000004023F4 0 (%d):%s() Process found %S
000000001420 000000402420 0 TriggerCmd
00000000142C 00000040242C 0 (%d):%s() cmd created
000000001464 000000402464 0 (%d):%s() data wrote
0000000014A0 0000004024A0 0 (%d):%s() failed to write parameters iNumArgs = %d
0000000014D4 0000004024D4 0 (%d):%s() Invalid num args
00000000163E 00000040263E 0 PathRemoveFileSpecW
000000001654 000000402654 0 PathAddBackslashW
000000001666 000000402666 0 SHLWAPI.dll
000000001674 000000402674 0 VirtualFreeEx
000000001684 000000402684 0 VirtualAllocEx
000000001696 000000402696 0 WriteProcessMemory
0000000016AC 0000004026AC 0 GetCommandLineW
0000000016BE 0000004026BE 0 SetFilePointer
0000000016D0 0000004026D0 0 lstrlenA
0000000016DC 0000004026DC 0 WaitForSingleObject
0000000016F2 0000004026F2 0 GetModuleHandleW
000000001706 000000402706 0 CreateRemoteThread
00000000171C 00000040271C 0 WriteFile
000000001728 000000402728 0 OpenProcess
000000001736 000000402736 0 GetModuleFileNameW
00000000174C 00000040274C 0 CreateFileW
00000000175A 00000040275A 0 WritePrivateProfileStringW
000000001778 000000402778 0 GetLastError
000000001788 000000402788 0 GetProcAddress
00000000179A 00000040279A 0 Process32FirstW
0000000017AC 0000004027AC 0 GetExitCodeThread
0000000017C0 0000004027C0 0 Process32NextW
0000000017D2 0000004027D2 0 lstrcmpiW
0000000017DE 0000004027DE 0 lstrcatW
0000000017EA 0000004027EA 0 CreateToolhelp32Snapshot
000000001806 000000402806 0 CloseHandle
000000001814 000000402814 0 LocalFree
000000001820 000000402820 0 lstrcpyW
00000000182A 00000040282A 0 KERNEL32.dll
00000000183A 00000040283A 0 wsprintfA
000000001844 000000402844 0 USER32.dll
000000001852 000000402852 0 InitializeSecurityDescriptor
000000001872 000000402872 0 SetSecurityDescriptorDacl
00000000188C 00000040288C 0 ADVAPI32.dll
00000000189C 00000040289C 0 CommandLineToArgvW
0000000018B0 0000004028B0 0 SHELL32.dll
0000000018BE 0000004028BE 0 IsProcessorFeaturePresent
000000001A56 000000403056 0 YYYYY
000000001A62 000000403062 0 YYYYYYYYYYYY
000000001A70 000000403070 0 }YPPPPYYYYa
000000001A86 000000403086 0 YYYYYYYYYYY
File pos Mem pos ID Text
======== ======= == ====
000000001B38 000000403138 0 JJJJKRJJJJOLJJJJJJJJUE@JJJEYMFJ]JJJJJJJJJJJJJJacgNJJkmJJEmJJDEJJ
00000000200B 00000040500B 0 0;0B0[0k0z0
000000002019 000000405019 0 1C1K1P1X1
000000002023 000000405023 0 1e1u1z1
000000002037 000000405037 0 2-2L2U2e2l2
000000002055 000000405055 0 3F3V3f3
00000000206B 00000040506B 0 434C4S4q4
000000002085 000000405085 0 535?5O5V5|5
00000000209D 00000040509D 0 6#616>6K6[6v6
0000000020B5 0000004050B5 0 767<7L7d7l7r7w7
0000000020DD 0000004050DD 0 8/868b8i8y8~8
000000001094 000000402094 0 C:\ATM\tlogsr.log
0000000010B8 0000004020B8 0 C:\ATM\c.ini
0000000010E4 0000004020E4 0 kernel32.dll
000000001410 000000402410 0 dll.dll
00000000147C 00000040247C 0 currency
000000001490 000000402490 0 amount
0000000014F0 0000004024F0 0 /load
0000000014FC 0000004024FC 0 atmapp.exe
000000001520 000000402520 0 /unload
=== DOWNLOAD ===
Mirror provided by vx-underground.org, thx!
=== PEDUMP REPORT ===
=== MZ Header ===
signature: "MZ"
bytes_in_last_block: 144 0x90
blocks_in_file: 3 3
num_relocs: 0 0
header_paragraphs: 4 4
min_extra_paragraphs: 0 0
max_extra_paragraphs: 65535 0xffff
ss: 0 0
sp: 184 0xb8
checksum: 0 0
ip: 0 0
cs: 0 0
reloc_table_offset: 64 0x40
overlay_number: 0 0
reserved0: 0 0
oem_id: 0 0
oem_info: 0 0
reserved2: 0 0
reserved3: 0 0
reserved4: 0 0
reserved5: 0 0
reserved6: 0 0
lfanew: 216 0xd8
=== DOS STUB ===
00000000: 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th|
00000010: 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|
00000020: 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |
00000030: 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|
=== RICH Header ===
LIB_ID VERSION TIMES_USED
158 9e 40219 9d1b 1 1
170 aa 40219 9d1b 2 2
147 93 30729 7809 11 b
1 1 0 0 34 22
175 af 40219 9d1b 3 3
157 9d 40219 9d1b 1 1
=== PE Header ===
signature: "PE\x00\x00"
# IMAGE_FILE_HEADER:
Machine: 332 0x14c x86
NumberOfSections: 5 5
TimeDateStamp: "2013-11-01 14:33:23"
PointerToSymbolTable: 0 0
NumberOfSymbols: 0 0
SizeOfOptionalHeader: 224 0xe0
Characteristics: 258 0x102 EXECUTABLE_IMAGE, 32BIT_MACHINE
# IMAGE_OPTIONAL_HEADER32:
Magic: 267 0x10b 32-bit executable
LinkerVersion: 10.0
SizeOfCode: 3072 0xc00
SizeOfInitializedData: 4608 0x1200
SizeOfUninitializedData: 0 0
AddressOfEntryPoint: 6224 0x1850
BaseOfCode: 4096 0x1000
BaseOfData: 8192 0x2000
ImageBase: 4194304 0x400000
SectionAlignment: 4096 0x1000
FileAlignment: 512 0x200
OperatingSystemVersion: 5.1
ImageVersion: 0.0
SubsystemVersion: 5.1
Reserved1: 0 0
SizeOfImage: 24576 0x6000
SizeOfHeaders: 1024 0x400
CheckSum: 0 0
Subsystem: 2 2 WINDOWS_GUI
DllCharacteristics: 34112 0x8540 DYNAMIC_BASE, NX_COMPAT, NO_SEH
TERMINAL_SERVER_AWARE
SizeOfStackReserve: 1048576 0x100000
SizeOfStackCommit: 4096 0x1000
SizeOfHeapReserve: 1048576 0x100000
SizeOfHeapCommit: 4096 0x1000
LoaderFlags: 0 0
NumberOfRvaAndSizes: 16 0x10
=== DATA DIRECTORY ===
EXPORT rva:0x 0 size:0x 0
IMPORT rva:0x 2530 size:0x 78
RESOURCE rva:0x 0 size:0x 0
EXCEPTION rva:0x 0 size:0x 0
SECURITY rva:0x 0 size:0x 0
BASERELOC rva:0x 5000 size:0x 110
DEBUG rva:0x 0 size:0x 0
ARCHITECTURE rva:0x 0 size:0x 0
GLOBALPTR rva:0x 0 size:0x 0
TLS rva:0x 0 size:0x 0
LOAD_CONFIG rva:0x 0 size:0x 0
Bound_IAT rva:0x 0 size:0x 0
IAT rva:0x 2000 size:0x 94
Delay_IAT rva:0x 0 size:0x 0
CLR_Header rva:0x 0 size:0x 0
rva:0x 0 size:0x 0
=== SECTIONS ===
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
.text 1000 a24 c00 400 0 0 0 0 60000020 R-X CODE
.rdata 2000 8d8 a00 1000 0 0 0 0 40000040 R-- IDATA
.data 3000 214 400 1a00 0 0 0 0 c0000040 RW- IDATA
.CRT 4000 4 200 1e00 0 0 0 0 40000040 R-- IDATA
.reloc 5000 162 200 2000 0 0 0 0 42000040 R-- IDATA DISCARDABLE
=== IMPORTS ===
MODULE_NAME HINT ORD FUNCTION_NAME
SHLWAPI.dll 30 PathAddBackslashW
SHLWAPI.dll 8b PathRemoveFileSpecW
KERNEL32.dll 4ed VirtualFreeEx
KERNEL32.dll 4ea VirtualAllocEx
KERNEL32.dll 52e WriteProcessMemory
KERNEL32.dll 187 GetCommandLineW
KERNEL32.dll 466 SetFilePointer
KERNEL32.dll 54d lstrlenA
KERNEL32.dll 4f9 WaitForSingleObject
KERNEL32.dll 218 GetModuleHandleW
KERNEL32.dll a9 CreateRemoteThread
KERNEL32.dll 525 WriteFile
KERNEL32.dll 380 OpenProcess
KERNEL32.dll 214 GetModuleFileNameW
KERNEL32.dll 8f CreateFileW
KERNEL32.dll 52b WritePrivateProfileStringW
KERNEL32.dll 304 IsProcessorFeaturePresent
KERNEL32.dll 245 GetProcAddress
KERNEL32.dll 396 Process32FirstW
KERNEL32.dll 1e0 GetExitCodeThread
KERNEL32.dll 398 Process32NextW
KERNEL32.dll 545 lstrcmpiW
KERNEL32.dll 53f lstrcatW
KERNEL32.dll be CreateToolhelp32Snapshot
KERNEL32.dll 52 CloseHandle
KERNEL32.dll 348 LocalFree
KERNEL32.dll 548 lstrcpyW
KERNEL32.dll 202 GetLastError
USER32.dll 332 wsprintfA
ADVAPI32.dll 2b6 SetSecurityDescriptorDacl
ADVAPI32.dll 177 InitializeSecurityDescriptor
SHELL32.dll 6 CommandLineToArgvW
=== Strings ===
File pos Mem pos ID Text
======== ======= == ====
00000000004D 00000040004D 0 !This program cannot be run in DOS mode.
0000000000BF 0000004000BF 0 .Rich
0000000001D0 0000004001D0 0 .text
0000000001F8 0000004001F8 0 .rdata
00000000021F 00000040021F 0 @.data
00000000026F 00000040026F 0 @.reloc
000000000980 000000401580 0 Whh#@
000000000A74 000000401674 0 Phh#@
000000000B3A 00000040173A 0 Wh $@
000000000B70 000000401770 0 RhD$@
000000000B94 000000401794 0 |Wh $@
000000000BC5 0000004017C5 0 Ph|$@
000000000BF0 0000004017F0 0 Rh $@
0000000010D4 0000004020D4 0 LoadLibraryW
000000001100 000000402100 0 FreeLibrary
00000000110C 00000040210C 0 GetLastError
00000000111C 00000040211C 0 InjectDll
000000001128 000000402128 0 (%d):%s() Failed to write shellcode to process
000000001158 000000402158 0 (%d):%s() Failed to write params to process
000000001188 000000402188 0 (%d):%s() InitializeSecurityDescriptor - failed %d
0000000011BC 0000004021BC 0 (%d):%s() SetSecurityDescriptorDacl() error %d
0000000011EC 0000004021EC 0 (%d):%s() Remote thread created, waiting unloadevent signal
00000000122C 00000040222C 0 (%d):%s() Failed to get exit code thread
000000001258 000000402258 0 (%d):%s() Thread job done, exit code thread %d
000000001288 000000402288 0 (%d):%s() Try unload library/shellcode
0000000012B0 0000004022B0 0 (%d):%s() Thread created, waiting for thread exit
0000000012E4 0000004022E4 0 (%d):%s() Done, unload library thread exit code = %d
00000000131C 00000040231C 0 (%d):%s() Release remote process memory
000000001348 000000402348 0 (%d):%s() Open process failed
000000001368 000000402368 0 SearchAndInject
000000001378 000000402378 0 (%d):%s() CreateToolhelp32Snapshot
00000000139C 00000040239C 0 (%d):%s() Parsing processes
0000000013BC 0000004023BC 0 (%d):%s() -------------------------------------------
0000000013F4 0000004023F4 0 (%d):%s() Process found %S
000000001420 000000402420 0 TriggerCmd
00000000142C 00000040242C 0 (%d):%s() cmd created
000000001464 000000402464 0 (%d):%s() data wrote
0000000014A0 0000004024A0 0 (%d):%s() failed to write parameters iNumArgs = %d
0000000014D4 0000004024D4 0 (%d):%s() Invalid num args
00000000163E 00000040263E 0 PathRemoveFileSpecW
000000001654 000000402654 0 PathAddBackslashW
000000001666 000000402666 0 SHLWAPI.dll
000000001674 000000402674 0 VirtualFreeEx
000000001684 000000402684 0 VirtualAllocEx
000000001696 000000402696 0 WriteProcessMemory
0000000016AC 0000004026AC 0 GetCommandLineW
0000000016BE 0000004026BE 0 SetFilePointer
0000000016D0 0000004026D0 0 lstrlenA
0000000016DC 0000004026DC 0 WaitForSingleObject
0000000016F2 0000004026F2 0 GetModuleHandleW
000000001706 000000402706 0 CreateRemoteThread
00000000171C 00000040271C 0 WriteFile
000000001728 000000402728 0 OpenProcess
000000001736 000000402736 0 GetModuleFileNameW
00000000174C 00000040274C 0 CreateFileW
00000000175A 00000040275A 0 WritePrivateProfileStringW
000000001778 000000402778 0 GetLastError
000000001788 000000402788 0 GetProcAddress
00000000179A 00000040279A 0 Process32FirstW
0000000017AC 0000004027AC 0 GetExitCodeThread
File pos Mem pos ID Text
======== ======= == ====
0000000017C0 0000004027C0 0 Process32NextW
0000000017D2 0000004027D2 0 lstrcmpiW
0000000017DE 0000004027DE 0 lstrcatW
0000000017EA 0000004027EA 0 CreateToolhelp32Snapshot
000000001806 000000402806 0 CloseHandle
000000001814 000000402814 0 LocalFree
000000001820 000000402820 0 lstrcpyW
00000000182A 00000040282A 0 KERNEL32.dll
00000000183A 00000040283A 0 wsprintfA
000000001844 000000402844 0 USER32.dll
000000001852 000000402852 0 InitializeSecurityDescriptor
000000001872 000000402872 0 SetSecurityDescriptorDacl
00000000188C 00000040288C 0 ADVAPI32.dll
00000000189C 00000040289C 0 CommandLineToArgvW
0000000018B0 0000004028B0 0 SHELL32.dll
0000000018BE 0000004028BE 0 IsProcessorFeaturePresent
000000001A56 000000403056 0 YYYYY
000000001A62 000000403062 0 YYYYYYYYYYYY
000000001A70 000000403070 0 }YPPPPYYYYa
000000001A86 000000403086 0 YYYYYYYYYYY
000000001B38 000000403138 0 JJJJKRJJJJOLJJJJJJJJUE@JJJEYMFJ]JJJJJJJJJJJJJJacgNJJkmJJEmJJDEJJ
00000000200B 00000040500B 0 0;0B0[0k0z0
000000002019 000000405019 0 1C1K1P1X1
000000002023 000000405023 0 1e1u1z1
000000002037 000000405037 0 2-2L2U2e2l2
000000002055 000000405055 0 3F3V3f3
00000000206B 00000040506B 0 434C4S4q4
000000002085 000000405085 0 535?5O5V5|5
00000000209D 00000040509D 0 6#616>6K6[6v6
0000000020B5 0000004050B5 0 767<7L7d7l7r7w7
0000000020DD 0000004050DD 0 8/868b8i8y8~8
000000001094 000000402094 0 C:\ATM\tlogsr.log
0000000010B8 0000004020B8 0 C:\ATM\c.ini
0000000010E4 0000004020E4 0 kernel32.dll
000000001410 000000402410 0 dll.dll
00000000147C 00000040247C 0 currency
000000001490 000000402490 0 amount
0000000014F0 0000004024F0 0 /load
0000000014FC 0000004024FC 0 atmapp.exe
000000001520 000000402520 0 /unload
00000000004D 00000040004D 0 !This program cannot be run in DOS mode.
0000000000BF 0000004000BF 0 .Rich
0000000001D0 0000004001D0 0 .text
0000000001F8 0000004001F8 0 .rdata
00000000021F 00000040021F 0 @.data
00000000026F 00000040026F 0 @.reloc
000000000980 000000401580 0 Whh#@
000000000A74 000000401674 0 Phh#@
000000000B3A 00000040173A 0 Wh $@
000000000B70 000000401770 0 RhD$@
000000000B94 000000401794 0 |Wh $@
000000000BC5 0000004017C5 0 Ph|$@
000000000BF0 0000004017F0 0 Rh $@
0000000010D4 0000004020D4 0 LoadLibraryW
000000001100 000000402100 0 FreeLibrary
00000000110C 00000040210C 0 GetLastError
00000000111C 00000040211C 0 InjectDll
000000001128 000000402128 0 (%d):%s() Failed to write shellcode to process
000000001158 000000402158 0 (%d):%s() Failed to write params to process
000000001188 000000402188 0 (%d):%s() InitializeSecurityDescriptor - failed %d
File pos Mem pos ID Text
======== ======= == ====
0000000011BC 0000004021BC 0 (%d):%s() SetSecurityDescriptorDacl() error %d
0000000011EC 0000004021EC 0 (%d):%s() Remote thread created, waiting unloadevent signal
00000000122C 00000040222C 0 (%d):%s() Failed to get exit code thread
000000001258 000000402258 0 (%d):%s() Thread job done, exit code thread %d
000000001288 000000402288 0 (%d):%s() Try unload library/shellcode
0000000012B0 0000004022B0 0 (%d):%s() Thread created, waiting for thread exit
0000000012E4 0000004022E4 0 (%d):%s() Done, unload library thread exit code = %d
00000000131C 00000040231C 0 (%d):%s() Release remote process memory
000000001348 000000402348 0 (%d):%s() Open process failed
000000001368 000000402368 0 SearchAndInject
000000001378 000000402378 0 (%d):%s() CreateToolhelp32Snapshot
00000000139C 00000040239C 0 (%d):%s() Parsing processes
0000000013BC 0000004023BC 0 (%d):%s() -------------------------------------------
0000000013F4 0000004023F4 0 (%d):%s() Process found %S
000000001420 000000402420 0 TriggerCmd
00000000142C 00000040242C 0 (%d):%s() cmd created
000000001464 000000402464 0 (%d):%s() data wrote
0000000014A0 0000004024A0 0 (%d):%s() failed to write parameters iNumArgs = %d
0000000014D4 0000004024D4 0 (%d):%s() Invalid num args
00000000163E 00000040263E 0 PathRemoveFileSpecW
000000001654 000000402654 0 PathAddBackslashW
000000001666 000000402666 0 SHLWAPI.dll
000000001674 000000402674 0 VirtualFreeEx
000000001684 000000402684 0 VirtualAllocEx
000000001696 000000402696 0 WriteProcessMemory
0000000016AC 0000004026AC 0 GetCommandLineW
0000000016BE 0000004026BE 0 SetFilePointer
0000000016D0 0000004026D0 0 lstrlenA
0000000016DC 0000004026DC 0 WaitForSingleObject
0000000016F2 0000004026F2 0 GetModuleHandleW
000000001706 000000402706 0 CreateRemoteThread
00000000171C 00000040271C 0 WriteFile
000000001728 000000402728 0 OpenProcess
000000001736 000000402736 0 GetModuleFileNameW
00000000174C 00000040274C 0 CreateFileW
00000000175A 00000040275A 0 WritePrivateProfileStringW
000000001778 000000402778 0 GetLastError
000000001788 000000402788 0 GetProcAddress
00000000179A 00000040279A 0 Process32FirstW
0000000017AC 0000004027AC 0 GetExitCodeThread
0000000017C0 0000004027C0 0 Process32NextW
0000000017D2 0000004027D2 0 lstrcmpiW
0000000017DE 0000004027DE 0 lstrcatW
0000000017EA 0000004027EA 0 CreateToolhelp32Snapshot
000000001806 000000402806 0 CloseHandle
000000001814 000000402814 0 LocalFree
000000001820 000000402820 0 lstrcpyW
00000000182A 00000040282A 0 KERNEL32.dll
00000000183A 00000040283A 0 wsprintfA
000000001844 000000402844 0 USER32.dll
000000001852 000000402852 0 InitializeSecurityDescriptor
000000001872 000000402872 0 SetSecurityDescriptorDacl
00000000188C 00000040288C 0 ADVAPI32.dll
00000000189C 00000040289C 0 CommandLineToArgvW
0000000018B0 0000004028B0 0 SHELL32.dll
0000000018BE 0000004028BE 0 IsProcessorFeaturePresent
000000001A56 000000403056 0 YYYYY
000000001A62 000000403062 0 YYYYYYYYYYYY
000000001A70 000000403070 0 }YPPPPYYYYa
000000001A86 000000403086 0 YYYYYYYYYYY
File pos Mem pos ID Text
======== ======= == ====
000000001B38 000000403138 0 JJJJKRJJJJOLJJJJJJJJUE@JJJEYMFJ]JJJJJJJJJJJJJJacgNJJkmJJEmJJDEJJ
00000000200B 00000040500B 0 0;0B0[0k0z0
000000002019 000000405019 0 1C1K1P1X1
000000002023 000000405023 0 1e1u1z1
000000002037 000000405037 0 2-2L2U2e2l2
000000002055 000000405055 0 3F3V3f3
00000000206B 00000040506B 0 434C4S4q4
000000002085 000000405085 0 535?5O5V5|5
00000000209D 00000040509D 0 6#616>6K6[6v6
0000000020B5 0000004050B5 0 767<7L7d7l7r7w7
0000000020DD 0000004050DD 0 8/868b8i8y8~8
000000001094 000000402094 0 C:\ATM\tlogsr.log
0000000010B8 0000004020B8 0 C:\ATM\c.ini
0000000010E4 0000004020E4 0 kernel32.dll
000000001410 000000402410 0 dll.dll
00000000147C 00000040247C 0 currency
000000001490 000000402490 0 amount
0000000014F0 0000004024F0 0 /load
0000000014FC 0000004024FC 0 atmapp.exe
000000001520 000000402520 0 /unload
=== DOWNLOAD ===
Mirror provided by vx-underground.org, thx!