
.- - -----÷M÷E÷N÷U÷------------------------------------------------------------- --- ---- -------------.
! WALL ! STATS ! GOODIES ! YARA ! FAQ ! RSS ! EMV !
`-------------- - --- ---------- -------- -------- -------- -------- ----------------- - ---- ---- --'
ATM MALWARE NOTICE
c3a5c8e9195163cef8e0e70bd8f3d49c8048e37af7c969341e1753aee63df0ae
Date...........: 2018-05-16
Family.........: WinPot
File name......: 777.exe
File size......: 30.00 KB
Type file......: EXE/Windows
Virscan........: VT - HA
Documentation..: https://medium.com/@pushret/atmjackpot-malware-en-b0cdb29e7ce
Additional note: Unusual DOS Stub, dispense per 55 notes.
Entropy:
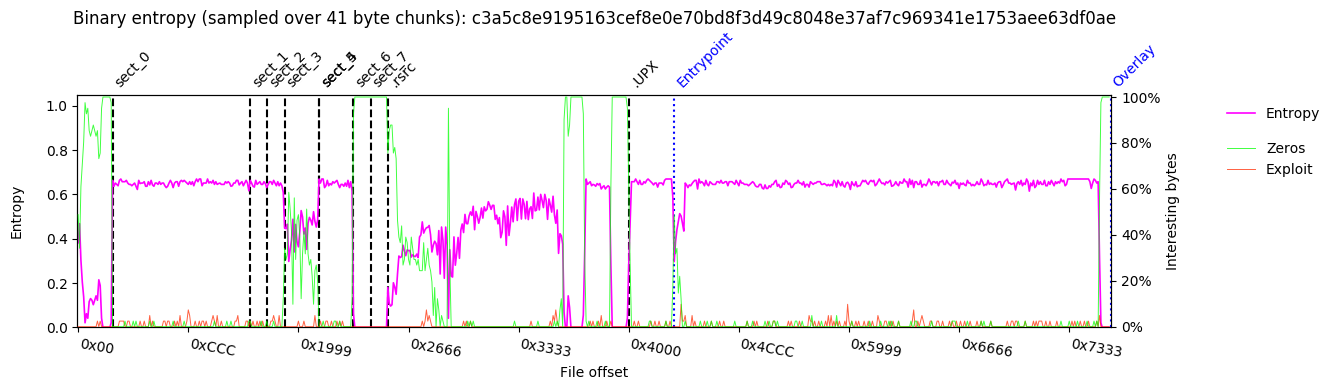 Binary Histogram:
Binary Histogram:
 === SCREENSHOT ===
=== SCREENSHOT ===
 === PEDUMP REPORT ===
=== PEDUMP REPORT ===
=== MZ Header ===
signature: "MZ"
bytes_in_last_block: 64 0x40
blocks_in_file: 1 1
num_relocs: 0 0
header_paragraphs: 2 2
min_extra_paragraphs: 4 4
max_extra_paragraphs: 65535 0xffff
ss: 2 2
sp: 64 0x40
checksum: 0 0
ip: 14 0xe
cs: 0 0
reloc_table_offset: 28 0x1c
overlay_number: 0 0
reserved0: 3706015365755568128 0x336e695700000000
oem_id: 8242 0x2032
oem_info: 28271 0x6e6f
reserved2: 220297580 0xd21796c
reserved3: 3020825610 0xb40e240a
reserved4: 47625 0xba09
reserved5: 3089222943 0xb821cd1f
reserved6: 567102465 0x21cd4c01
lfanew: 64 0x40
=== DOS STUB ===
00000000: 57 69 6e 33 32 20 6f 6e 6c 79 21 0d 0a 24 0e b4 |Win32 only!..$..|
00000010: 09 ba 00 00 1f cd 21 b8 01 4c cd 21 40 00 00 00 |......!..L.!@...|
=== PE Header ===
signature: "PE\x00\x00"
# IMAGE_FILE_HEADER:
Machine: 332 0x14c x86
NumberOfSections: 10 0xa
TimeDateStamp: "2026-01-14 09:44:18"
PointerToSymbolTable: 0 0
NumberOfSymbols: 0 0
SizeOfOptionalHeader: 224 0xe0
Characteristics: 783 0x30f RELOCS_STRIPPED, EXECUTABLE_IMAGE
LINE_NUMS_STRIPPED, LOCAL_SYMS_STRIPPED
32BIT_MACHINE, DEBUG_STRIPPED
# IMAGE_OPTIONAL_HEADER32:
Magic: 267 0x10b 32-bit executable
LinkerVersion: 2.24
SizeOfCode: 8192 0x2000
SizeOfInitializedData: 20992 0x5200
SizeOfUninitializedData: 512 0x200
AddressOfEntryPoint: 50505 0xc549
BaseOfCode: 4096 0x1000
BaseOfData: 12288 0x3000
ImageBase: 4194304 0x400000
SectionAlignment: 4096 0x1000
FileAlignment: 512 0x200
OperatingSystemVersion: 4.0
ImageVersion: 1.0
SubsystemVersion: 4.0
Reserved1: 0 0
SizeOfImage: 86016 0x15000
SizeOfHeaders: 1024 0x400
CheckSum: 67975 0x10987
Subsystem: 2 2 WINDOWS_GUI
DllCharacteristics: 0 0
SizeOfStackReserve: 2097152 0x200000
SizeOfStackCommit: 4096 0x1000
SizeOfHeapReserve: 1048576 0x100000
SizeOfHeapCommit: 4096 0x1000
LoaderFlags: 0 0
NumberOfRvaAndSizes: 16 0x10
=== DATA DIRECTORY ===
EXPORT rva:0x 0 size:0x 0
IMPORT rva:0x c000 size:0x 60
RESOURCE rva:0x a000 size:0x 1a18
EXCEPTION rva:0x 0 size:0x 0
SECURITY rva:0x 0 size:0x 0
BASERELOC rva:0x 0 size:0x 0
DEBUG rva:0x 0 size:0x 0
ARCHITECTURE rva:0x 0 size:0x 0
GLOBALPTR rva:0x 0 size:0x 0
TLS rva:0x f6d9 size:0x 18
LOAD_CONFIG rva:0x 0 size:0x 0
Bound_IAT rva:0x 0 size:0x 0
IAT rva:0x 0 size:0x 0
Delay_IAT rva:0x 0 size:0x 0
CLR_Header rva:0x 0 size:0x 0
rva:0x 0 size:0x 0
=== SECTIONS ===
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
1000 2000 1000 400 0 0 0 0 c0000040 RW- IDATA
3000 1000 200 1400 0 0 0 0 c0000040 RW- IDATA
4000 1000 200 1600 0 0 0 0 c0000040 RW- IDATA
5000 1000 400 1800 0 0 0 0 c0000040 RW- IDATA
6000 1000 0 1c00 0 0 0 0 c0000040 RW- IDATA
7000 1000 400 1c00 0 0 0 0 c0000040 RW- IDATA
8000 1000 200 2000 0 0 0 0 c0000040 RW- IDATA
9000 1000 200 2200 0 0 0 0 c0000040 RW- IDATA
.rsrc a000 2000 1c00 2400 0 0 0 0 c0000040 RW- IDATA
.UPX c000 9000 3800 4000 0 0 0 0 c0000040 RW- IDATA
=== TLS ===
RAW_START RAW_END INDEX CALLBKS ZEROFILL FLAGS
409001 40901c 414000 408004 0 0
=== RESOURCES ===
FILE_OFFSET CP LANG SIZE TYPE NAME
0x24e8 0 0 5672 ICON #1
0x3b10 0 0 754 DIALOG #100
0x3e04 0 0 20 GROUP_ICON #102
[?] can't find file_offset of VA 0x14000
=== IMPORTS ===
MODULE_NAME HINT ORD FUNCTION_NAME
Kernel32.dll 0 LoadLibraryA
Kernel32.dll 0 GetProcAddress
=== Packer / Compiler ===
yoda's Protector v1.03.2(.dll,.ocx) (Ashkbiz Danehkar)
File pos Mem pos ID Text
======== ======= == ====
000000000020 000000400020 0 Win32 only!
000000000278 000000400278 0 .rsrc
0000000004BE 0000004010BE 0 htc>n
0000000005FB 0000004011FB 0 a<&MRuZ
0000000006DF 0000004012DF 0 >w.*e
0000000006E6 0000004012E6 0 u/d\A
000000000985 000000401585 0 %v(=*"
0000000009E5 0000004015E5 0 \_MG_
000000000B19 000000401719 0 Gf.6xs6P
000000000B39 000000401739 0 >gY+m[qq,)7u
000000000BFA 0000004017FA 0 f,]8B
000000000C43 000000401843 0 DOLKG
000000000D85 000000401985 0 V\~ET
000000000DE0 0000004019E0 0 RZ~P)
000000000E41 000000401A41 0 R<~/J
000000000EA7 000000401AA7 0 KpZ5+
000000000F95 000000401B95 0 ~R[tN*
00000000120C 000000401E0C 0 &53qW
0000000013EE 000000401FEE 0 b~+*es
00000000158B 00000040318B 0 ],I*:
0000000017B6 0000004041B6 0 V7pThl\
000000001D1E 00000040711E 0 hUL 0'
000000001D93 000000407193 0 ,_{bM
000000001ECA 0000004072CA 0 .RvT]MM
000000001FF8 0000004073F8 0 FUtAM
00000000293D 00000040A53D 0 &&&&&&&&&
0000000029A5 00000040A5A5 0 QQQQQ
0000000029BB 00000040A5BB 0 &&&&&&&&&
0000000029DA 00000040A5DA 0 ?????????QQQQ
0000000029FA 00000040A5FA 0 QQQ?????????
000000002A23 00000040A623 0 NNNNN:::::::::::::::::::::NNN
000000002A59 00000040A659 0 [[[[[
000000002BC1 00000040A7C1 0 =======
000000002C10 00000040A810 0 QQQ :
000000002C50 00000040A850 0 QQ? :
000000002C90 00000040A890 0 QQ? :\
00000000309A 00000040AC9A 0 ]]]]]]]]
0000000030AC 00000040ACAC 0 ]]]]]]]]]
0000000030EB 00000040ACEB 0 LL_____
0000000030F3 00000040ACF3 0 LLLLX
0000000030FC 00000040ACFC 0 VXXXLXXXXXXXV
00000000322B 00000040AE2B 0 '''''''''''''
00000000325A 00000040AE5A 0 YYY::Y:NNNNddcccd
000000003428 00000040B028 0 #N#ff
0000000035A0 00000040B1A0 0 N*++BBB*
000000003615 00000040B215 0 iNi##
0000000036A2 00000040B2A2 0 :bgbf
0000000036B1 00000040B2B1 0 iAcfb
0000000036E6 00000040B2E6 0 & Q#
000000003723 00000040B323 0 bAp88(
000000003754 00000040B354 0 Ncdc:N
000000003823 00000040B423 0 &&&&&
00000000387F 00000040B47F 0
000000003B8D 00000040B78D 0 !"I$'&P(M*+,
000000003B9D 00000040B79D 0 0C23456489j;<=>x@@BlDhFGH
000000003BBB 00000040B7BB 0 NOPQRPTU
000000003BCF 00000040B7CF 0 bcd:;
000000003BD5 00000040B7D5 0 hujklmnlpq
000000003BE0 00000040B7E0 0 stuvvx
000000003BEB 00000040B7EB 0 ~j|VW
File pos Mem pos ID Text
======== ======= == ====
000000003C8C 00000040B88C 0 e !"#$%&'((b+,-.d042O4/684
000000003CA9 00000040B8A9 0 <n>o@
000000003CB1 00000040B8B1 0 DEFGHIJKLL
000000003CC1 00000040B8C1 0 TXVsXSZWX23
000000003CD5 00000040B8D5 0 hijklmnnpq
000000003CE0 00000040B8E0 0 stuvtx
000000003CEB 00000040B8EB 0 ~||VW
000000003D8D 00000040B98D 0 9"C$.&1$
000000003D99 00000040B999 0 ,-./012245f789:
000000003DAB 00000040B9AB 0 >_@JB/@
000000003DB5 00000040B9B5 0 HIJKLMNOPP
000000003DD9 00000040B9D9 0 lmnopqrstt
000000003DE4 00000040B9E4 0 wxyzv|
000000004028 00000040C028 0 Kernel32.dll
000000004041 00000040C041 0 LoadLibraryA
00000000404F 00000040C04F 0 GetProcAddress
0000000040B9 00000040C0B9 0 .>GVm
000000004414 00000040C414 0 VRwqB
000000004847 00000040C847 0 VE?rt
00000000488F 00000040C88F 0 x<TF{
000000004918 00000040C918 0 c&(mM
000000004AEB 00000040CAEB 0 aAhBb
000000004B0C 00000040CB0C 0 N#%Z:
000000004B4B 00000040CB4B 0 ge+5jJ
000000004C14 00000040CC14 0 i-'lo
000000004DD7 00000040CDD7 0 z~JX]=$:
000000004DFC 00000040CDFC 0 yK!fF
000000004F3B 00000040CF3B 0 cxv1v
000000004F8C 00000040CF8C 0 ]#F_NDF{
000000004FF7 00000040CFF7 0 ixJ e
0000000050D3 00000040D0D3 0 pRQW\
0000000050E0 00000040D0E0 0 P_J_b
000000005316 00000040D316 0 ,p_k-b
000000005466 00000040D466 0 cn1u<
000000005476 00000040D476 0 gr5i@
000000005603 00000040D603 0 |n!#h
000000005631 00000040D631 0 s.sS6,t
000000005737 00000040D737 0 lwN%;b
000000005AA6 00000040DAA6 0 Vcf4Oj
00000000614B 00000040E14B 0 ,,,EX
00000000619F 00000040E19F 0 $*\D>e
0000000061CF 00000040E1CF 0 0FhP:q
000000006572 00000040E572 0 Ck|10
00000000660B 00000040E60B 0 abWVD
000000006744 00000040E744 0 iu-|i
00000000696E 00000040E96E 0 @k6s>
000000006C72 00000040EC72 0 fq4x?
000000006CC6 00000040ECC6 0 X\{gI
000000006E66 00000040EE66 0 2\fr5
000000006E8C 00000040EE8C 0 S_>8$P
000000007146 00000040F146 0 /R va
0000000072A4 00000040F2A4 0 du3YX
000000000020 000000400020 0 Win32 only!
000000000278 000000400278 0 .rsrc
0000000004BE 0000004010BE 0 htc>n
0000000005FB 0000004011FB 0 a<&MRuZ
0000000006DF 0000004012DF 0 >w.*e
0000000006E6 0000004012E6 0 u/d\A
000000000985 000000401585 0 %v(=*"
0000000009E5 0000004015E5 0 \_MG_
File pos Mem pos ID Text
======== ======= == ====
000000000B19 000000401719 0 Gf.6xs6P
000000000B39 000000401739 0 >gY+m[qq,)7u
000000000BFA 0000004017FA 0 f,]8B
000000000C43 000000401843 0 DOLKG
000000000D85 000000401985 0 V\~ET
000000000DE0 0000004019E0 0 RZ~P)
000000000E41 000000401A41 0 R<~/J
000000000EA7 000000401AA7 0 KpZ5+
000000000F95 000000401B95 0 ~R[tN*
00000000120C 000000401E0C 0 &53qW
0000000013EE 000000401FEE 0 b~+*es
00000000158B 00000040318B 0 ],I*:
0000000017B6 0000004041B6 0 V7pThl\
000000001D1E 00000040711E 0 hUL 0'
000000001D93 000000407193 0 ,_{bM
000000001ECA 0000004072CA 0 .RvT]MM
000000001FF8 0000004073F8 0 FUtAM
00000000293D 00000040A53D 0 &&&&&&&&&
0000000029A5 00000040A5A5 0 QQQQQ
0000000029BB 00000040A5BB 0 &&&&&&&&&
0000000029DA 00000040A5DA 0 ?????????QQQQ
0000000029FA 00000040A5FA 0 QQQ?????????
000000002A23 00000040A623 0 NNNNN:::::::::::::::::::::NNN
000000002A59 00000040A659 0 [[[[[
000000002BC1 00000040A7C1 0 =======
000000002C10 00000040A810 0 QQQ :
000000002C50 00000040A850 0 QQ? :
000000002C90 00000040A890 0 QQ? :\
00000000309A 00000040AC9A 0 ]]]]]]]]
0000000030AC 00000040ACAC 0 ]]]]]]]]]
0000000030EB 00000040ACEB 0 LL_____
0000000030F3 00000040ACF3 0 LLLLX
0000000030FC 00000040ACFC 0 VXXXLXXXXXXXV
00000000322B 00000040AE2B 0 '''''''''''''
00000000325A 00000040AE5A 0 YYY::Y:NNNNddcccd
000000003428 00000040B028 0 #N#ff
0000000035A0 00000040B1A0 0 N*++BBB*
000000003615 00000040B215 0 iNi##
0000000036A2 00000040B2A2 0 :bgbf
0000000036B1 00000040B2B1 0 iAcfb
0000000036E6 00000040B2E6 0 & Q#
000000003723 00000040B323 0 bAp88(
000000003754 00000040B354 0 Ncdc:N
000000003823 00000040B423 0 &&&&&
00000000387F 00000040B47F 0
000000003B8D 00000040B78D 0 !"I$'&P(M*+,
000000003B9D 00000040B79D 0 0C23456489j;<=>x@@BlDhFGH
000000003BBB 00000040B7BB 0 NOPQRPTU
000000003BCF 00000040B7CF 0 bcd:;
000000003BD5 00000040B7D5 0 hujklmnlpq
000000003BE0 00000040B7E0 0 stuvvx
000000003BEB 00000040B7EB 0 ~j|VW
000000003C8C 00000040B88C 0 e !"#$%&'((b+,-.d042O4/684
000000003CA9 00000040B8A9 0 <n>o@
000000003CB1 00000040B8B1 0 DEFGHIJKLL
000000003CC1 00000040B8C1 0 TXVsXSZWX23
000000003CD5 00000040B8D5 0 hijklmnnpq
000000003CE0 00000040B8E0 0 stuvtx
000000003CEB 00000040B8EB 0 ~||VW
000000003D8D 00000040B98D 0 9"C$.&1$
File pos Mem pos ID Text
======== ======= == ====
000000003D99 00000040B999 0 ,-./012245f789:
000000003DAB 00000040B9AB 0 >_@JB/@
000000003DB5 00000040B9B5 0 HIJKLMNOPP
000000003DD9 00000040B9D9 0 lmnopqrstt
000000003DE4 00000040B9E4 0 wxyzv|
000000004028 00000040C028 0 Kernel32.dll
000000004041 00000040C041 0 LoadLibraryA
00000000404F 00000040C04F 0 GetProcAddress
0000000040B9 00000040C0B9 0 .>GVm
000000004414 00000040C414 0 VRwqB
000000004847 00000040C847 0 VE?rt
00000000488F 00000040C88F 0 x<TF{
000000004918 00000040C918 0 c&(mM
000000004AEB 00000040CAEB 0 aAhBb
000000004B0C 00000040CB0C 0 N#%Z:
000000004B4B 00000040CB4B 0 ge+5jJ
000000004C14 00000040CC14 0 i-'lo
000000004DD7 00000040CDD7 0 z~JX]=$:
000000004DFC 00000040CDFC 0 yK!fF
000000004F3B 00000040CF3B 0 cxv1v
000000004F8C 00000040CF8C 0 ]#F_NDF{
000000004FF7 00000040CFF7 0 ixJ e
0000000050D3 00000040D0D3 0 pRQW\
0000000050E0 00000040D0E0 0 P_J_b
000000005316 00000040D316 0 ,p_k-b
000000005466 00000040D466 0 cn1u<
000000005476 00000040D476 0 gr5i@
000000005603 00000040D603 0 |n!#h
000000005631 00000040D631 0 s.sS6,t
000000005737 00000040D737 0 lwN%;b
000000005AA6 00000040DAA6 0 Vcf4Oj
00000000614B 00000040E14B 0 ,,,EX
00000000619F 00000040E19F 0 $*\D>e
0000000061CF 00000040E1CF 0 0FhP:q
000000006572 00000040E572 0 Ck|10
00000000660B 00000040E60B 0 abWVD
000000006744 00000040E744 0 iu-|i
00000000696E 00000040E96E 0 @k6s>
000000006C72 00000040EC72 0 fq4x?
000000006CC6 00000040ECC6 0 X\{gI
000000006E66 00000040EE66 0 2\fr5
000000006E8C 00000040EE8C 0 S_>8$P
000000007146 00000040F146 0 /R va
0000000072A4 00000040F2A4 0 du3YX

 Binary Histogram:
Binary Histogram:
 === SCREENSHOT ===
=== SCREENSHOT ===
 === PEDUMP REPORT ===
=== MZ Header ===
signature: "MZ"
bytes_in_last_block: 64 0x40
blocks_in_file: 1 1
num_relocs: 0 0
header_paragraphs: 2 2
min_extra_paragraphs: 4 4
max_extra_paragraphs: 65535 0xffff
ss: 2 2
sp: 64 0x40
checksum: 0 0
ip: 14 0xe
cs: 0 0
reloc_table_offset: 28 0x1c
overlay_number: 0 0
reserved0: 3706015365755568128 0x336e695700000000
oem_id: 8242 0x2032
oem_info: 28271 0x6e6f
reserved2: 220297580 0xd21796c
reserved3: 3020825610 0xb40e240a
reserved4: 47625 0xba09
reserved5: 3089222943 0xb821cd1f
reserved6: 567102465 0x21cd4c01
lfanew: 64 0x40
=== DOS STUB ===
00000000: 57 69 6e 33 32 20 6f 6e 6c 79 21 0d 0a 24 0e b4 |Win32 only!..$..|
00000010: 09 ba 00 00 1f cd 21 b8 01 4c cd 21 40 00 00 00 |......!..L.!@...|
=== PE Header ===
signature: "PE\x00\x00"
# IMAGE_FILE_HEADER:
Machine: 332 0x14c x86
NumberOfSections: 10 0xa
TimeDateStamp: "2026-01-14 09:44:18"
PointerToSymbolTable: 0 0
NumberOfSymbols: 0 0
SizeOfOptionalHeader: 224 0xe0
Characteristics: 783 0x30f RELOCS_STRIPPED, EXECUTABLE_IMAGE
LINE_NUMS_STRIPPED, LOCAL_SYMS_STRIPPED
32BIT_MACHINE, DEBUG_STRIPPED
# IMAGE_OPTIONAL_HEADER32:
Magic: 267 0x10b 32-bit executable
LinkerVersion: 2.24
SizeOfCode: 8192 0x2000
SizeOfInitializedData: 20992 0x5200
SizeOfUninitializedData: 512 0x200
AddressOfEntryPoint: 50505 0xc549
BaseOfCode: 4096 0x1000
BaseOfData: 12288 0x3000
ImageBase: 4194304 0x400000
SectionAlignment: 4096 0x1000
FileAlignment: 512 0x200
OperatingSystemVersion: 4.0
ImageVersion: 1.0
SubsystemVersion: 4.0
Reserved1: 0 0
SizeOfImage: 86016 0x15000
SizeOfHeaders: 1024 0x400
CheckSum: 67975 0x10987
Subsystem: 2 2 WINDOWS_GUI
DllCharacteristics: 0 0
SizeOfStackReserve: 2097152 0x200000
SizeOfStackCommit: 4096 0x1000
SizeOfHeapReserve: 1048576 0x100000
SizeOfHeapCommit: 4096 0x1000
LoaderFlags: 0 0
NumberOfRvaAndSizes: 16 0x10
=== DATA DIRECTORY ===
EXPORT rva:0x 0 size:0x 0
IMPORT rva:0x c000 size:0x 60
RESOURCE rva:0x a000 size:0x 1a18
EXCEPTION rva:0x 0 size:0x 0
SECURITY rva:0x 0 size:0x 0
BASERELOC rva:0x 0 size:0x 0
DEBUG rva:0x 0 size:0x 0
ARCHITECTURE rva:0x 0 size:0x 0
GLOBALPTR rva:0x 0 size:0x 0
TLS rva:0x f6d9 size:0x 18
LOAD_CONFIG rva:0x 0 size:0x 0
Bound_IAT rva:0x 0 size:0x 0
IAT rva:0x 0 size:0x 0
Delay_IAT rva:0x 0 size:0x 0
CLR_Header rva:0x 0 size:0x 0
rva:0x 0 size:0x 0
=== SECTIONS ===
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
1000 2000 1000 400 0 0 0 0 c0000040 RW- IDATA
3000 1000 200 1400 0 0 0 0 c0000040 RW- IDATA
4000 1000 200 1600 0 0 0 0 c0000040 RW- IDATA
5000 1000 400 1800 0 0 0 0 c0000040 RW- IDATA
6000 1000 0 1c00 0 0 0 0 c0000040 RW- IDATA
7000 1000 400 1c00 0 0 0 0 c0000040 RW- IDATA
8000 1000 200 2000 0 0 0 0 c0000040 RW- IDATA
9000 1000 200 2200 0 0 0 0 c0000040 RW- IDATA
.rsrc a000 2000 1c00 2400 0 0 0 0 c0000040 RW- IDATA
.UPX c000 9000 3800 4000 0 0 0 0 c0000040 RW- IDATA
=== TLS ===
RAW_START RAW_END INDEX CALLBKS ZEROFILL FLAGS
409001 40901c 414000 408004 0 0
=== RESOURCES ===
FILE_OFFSET CP LANG SIZE TYPE NAME
0x24e8 0 0 5672 ICON #1
0x3b10 0 0 754 DIALOG #100
0x3e04 0 0 20 GROUP_ICON #102
[?] can't find file_offset of VA 0x14000
=== IMPORTS ===
MODULE_NAME HINT ORD FUNCTION_NAME
Kernel32.dll 0 LoadLibraryA
Kernel32.dll 0 GetProcAddress
=== Packer / Compiler ===
yoda's Protector v1.03.2(.dll,.ocx) (Ashkbiz Danehkar)
=== Strings ===
File pos Mem pos ID Text
======== ======= == ====
000000000020 000000400020 0 Win32 only!
000000000278 000000400278 0 .rsrc
0000000004BE 0000004010BE 0 htc>n
0000000005FB 0000004011FB 0 a<&MRuZ
0000000006DF 0000004012DF 0 >w.*e
0000000006E6 0000004012E6 0 u/d\A
000000000985 000000401585 0 %v(=*"
0000000009E5 0000004015E5 0 \_MG_
000000000B19 000000401719 0 Gf.6xs6P
000000000B39 000000401739 0 >gY+m[qq,)7u
000000000BFA 0000004017FA 0 f,]8B
000000000C43 000000401843 0 DOLKG
000000000D85 000000401985 0 V\~ET
000000000DE0 0000004019E0 0 RZ~P)
000000000E41 000000401A41 0 R<~/J
000000000EA7 000000401AA7 0 KpZ5+
000000000F95 000000401B95 0 ~R[tN*
00000000120C 000000401E0C 0 &53qW
0000000013EE 000000401FEE 0 b~+*es
00000000158B 00000040318B 0 ],I*:
0000000017B6 0000004041B6 0 V7pThl\
000000001D1E 00000040711E 0 hUL 0'
000000001D93 000000407193 0 ,_{bM
000000001ECA 0000004072CA 0 .RvT]MM
000000001FF8 0000004073F8 0 FUtAM
00000000293D 00000040A53D 0 &&&&&&&&&
0000000029A5 00000040A5A5 0 QQQQQ
0000000029BB 00000040A5BB 0 &&&&&&&&&
0000000029DA 00000040A5DA 0 ?????????QQQQ
0000000029FA 00000040A5FA 0 QQQ?????????
000000002A23 00000040A623 0 NNNNN:::::::::::::::::::::NNN
000000002A59 00000040A659 0 [[[[[
000000002BC1 00000040A7C1 0 =======
000000002C10 00000040A810 0 QQQ :
000000002C50 00000040A850 0 QQ? :
000000002C90 00000040A890 0 QQ? :\
00000000309A 00000040AC9A 0 ]]]]]]]]
0000000030AC 00000040ACAC 0 ]]]]]]]]]
0000000030EB 00000040ACEB 0 LL_____
0000000030F3 00000040ACF3 0 LLLLX
0000000030FC 00000040ACFC 0 VXXXLXXXXXXXV
00000000322B 00000040AE2B 0 '''''''''''''
00000000325A 00000040AE5A 0 YYY::Y:NNNNddcccd
000000003428 00000040B028 0 #N#ff
0000000035A0 00000040B1A0 0 N*++BBB*
000000003615 00000040B215 0 iNi##
0000000036A2 00000040B2A2 0 :bgbf
0000000036B1 00000040B2B1 0 iAcfb
0000000036E6 00000040B2E6 0 & Q#
000000003723 00000040B323 0 bAp88(
000000003754 00000040B354 0 Ncdc:N
000000003823 00000040B423 0 &&&&&
00000000387F 00000040B47F 0
000000003B8D 00000040B78D 0 !"I$'&P(M*+,
000000003B9D 00000040B79D 0 0C23456489j;<=>x@@BlDhFGH
000000003BBB 00000040B7BB 0 NOPQRPTU
000000003BCF 00000040B7CF 0 bcd:;
000000003BD5 00000040B7D5 0 hujklmnlpq
000000003BE0 00000040B7E0 0 stuvvx
000000003BEB 00000040B7EB 0 ~j|VW
File pos Mem pos ID Text
======== ======= == ====
000000003C8C 00000040B88C 0 e !"#$%&'((b+,-.d042O4/684
000000003CA9 00000040B8A9 0 <n>o@
000000003CB1 00000040B8B1 0 DEFGHIJKLL
000000003CC1 00000040B8C1 0 TXVsXSZWX23
000000003CD5 00000040B8D5 0 hijklmnnpq
000000003CE0 00000040B8E0 0 stuvtx
000000003CEB 00000040B8EB 0 ~||VW
000000003D8D 00000040B98D 0 9"C$.&1$
000000003D99 00000040B999 0 ,-./012245f789:
000000003DAB 00000040B9AB 0 >_@JB/@
000000003DB5 00000040B9B5 0 HIJKLMNOPP
000000003DD9 00000040B9D9 0 lmnopqrstt
000000003DE4 00000040B9E4 0 wxyzv|
000000004028 00000040C028 0 Kernel32.dll
000000004041 00000040C041 0 LoadLibraryA
00000000404F 00000040C04F 0 GetProcAddress
0000000040B9 00000040C0B9 0 .>GVm
000000004414 00000040C414 0 VRwqB
000000004847 00000040C847 0 VE?rt
00000000488F 00000040C88F 0 x<TF{
000000004918 00000040C918 0 c&(mM
000000004AEB 00000040CAEB 0 aAhBb
000000004B0C 00000040CB0C 0 N#%Z:
000000004B4B 00000040CB4B 0 ge+5jJ
000000004C14 00000040CC14 0 i-'lo
000000004DD7 00000040CDD7 0 z~JX]=$:
000000004DFC 00000040CDFC 0 yK!fF
000000004F3B 00000040CF3B 0 cxv1v
000000004F8C 00000040CF8C 0 ]#F_NDF{
000000004FF7 00000040CFF7 0 ixJ e
0000000050D3 00000040D0D3 0 pRQW\
0000000050E0 00000040D0E0 0 P_J_b
000000005316 00000040D316 0 ,p_k-b
000000005466 00000040D466 0 cn1u<
000000005476 00000040D476 0 gr5i@
000000005603 00000040D603 0 |n!#h
000000005631 00000040D631 0 s.sS6,t
000000005737 00000040D737 0 lwN%;b
000000005AA6 00000040DAA6 0 Vcf4Oj
00000000614B 00000040E14B 0 ,,,EX
00000000619F 00000040E19F 0 $*\D>e
0000000061CF 00000040E1CF 0 0FhP:q
000000006572 00000040E572 0 Ck|10
00000000660B 00000040E60B 0 abWVD
000000006744 00000040E744 0 iu-|i
00000000696E 00000040E96E 0 @k6s>
000000006C72 00000040EC72 0 fq4x?
000000006CC6 00000040ECC6 0 X\{gI
000000006E66 00000040EE66 0 2\fr5
000000006E8C 00000040EE8C 0 S_>8$P
000000007146 00000040F146 0 /R va
0000000072A4 00000040F2A4 0 du3YX
000000000020 000000400020 0 Win32 only!
000000000278 000000400278 0 .rsrc
0000000004BE 0000004010BE 0 htc>n
0000000005FB 0000004011FB 0 a<&MRuZ
0000000006DF 0000004012DF 0 >w.*e
0000000006E6 0000004012E6 0 u/d\A
000000000985 000000401585 0 %v(=*"
0000000009E5 0000004015E5 0 \_MG_
File pos Mem pos ID Text
======== ======= == ====
000000000B19 000000401719 0 Gf.6xs6P
000000000B39 000000401739 0 >gY+m[qq,)7u
000000000BFA 0000004017FA 0 f,]8B
000000000C43 000000401843 0 DOLKG
000000000D85 000000401985 0 V\~ET
000000000DE0 0000004019E0 0 RZ~P)
000000000E41 000000401A41 0 R<~/J
000000000EA7 000000401AA7 0 KpZ5+
000000000F95 000000401B95 0 ~R[tN*
00000000120C 000000401E0C 0 &53qW
0000000013EE 000000401FEE 0 b~+*es
00000000158B 00000040318B 0 ],I*:
0000000017B6 0000004041B6 0 V7pThl\
000000001D1E 00000040711E 0 hUL 0'
000000001D93 000000407193 0 ,_{bM
000000001ECA 0000004072CA 0 .RvT]MM
000000001FF8 0000004073F8 0 FUtAM
00000000293D 00000040A53D 0 &&&&&&&&&
0000000029A5 00000040A5A5 0 QQQQQ
0000000029BB 00000040A5BB 0 &&&&&&&&&
0000000029DA 00000040A5DA 0 ?????????QQQQ
0000000029FA 00000040A5FA 0 QQQ?????????
000000002A23 00000040A623 0 NNNNN:::::::::::::::::::::NNN
000000002A59 00000040A659 0 [[[[[
000000002BC1 00000040A7C1 0 =======
000000002C10 00000040A810 0 QQQ :
000000002C50 00000040A850 0 QQ? :
000000002C90 00000040A890 0 QQ? :\
00000000309A 00000040AC9A 0 ]]]]]]]]
0000000030AC 00000040ACAC 0 ]]]]]]]]]
0000000030EB 00000040ACEB 0 LL_____
0000000030F3 00000040ACF3 0 LLLLX
0000000030FC 00000040ACFC 0 VXXXLXXXXXXXV
00000000322B 00000040AE2B 0 '''''''''''''
00000000325A 00000040AE5A 0 YYY::Y:NNNNddcccd
000000003428 00000040B028 0 #N#ff
0000000035A0 00000040B1A0 0 N*++BBB*
000000003615 00000040B215 0 iNi##
0000000036A2 00000040B2A2 0 :bgbf
0000000036B1 00000040B2B1 0 iAcfb
0000000036E6 00000040B2E6 0 & Q#
000000003723 00000040B323 0 bAp88(
000000003754 00000040B354 0 Ncdc:N
000000003823 00000040B423 0 &&&&&
00000000387F 00000040B47F 0
000000003B8D 00000040B78D 0 !"I$'&P(M*+,
000000003B9D 00000040B79D 0 0C23456489j;<=>x@@BlDhFGH
000000003BBB 00000040B7BB 0 NOPQRPTU
000000003BCF 00000040B7CF 0 bcd:;
000000003BD5 00000040B7D5 0 hujklmnlpq
000000003BE0 00000040B7E0 0 stuvvx
000000003BEB 00000040B7EB 0 ~j|VW
000000003C8C 00000040B88C 0 e !"#$%&'((b+,-.d042O4/684
000000003CA9 00000040B8A9 0 <n>o@
000000003CB1 00000040B8B1 0 DEFGHIJKLL
000000003CC1 00000040B8C1 0 TXVsXSZWX23
000000003CD5 00000040B8D5 0 hijklmnnpq
000000003CE0 00000040B8E0 0 stuvtx
000000003CEB 00000040B8EB 0 ~||VW
000000003D8D 00000040B98D 0 9"C$.&1$
File pos Mem pos ID Text
======== ======= == ====
000000003D99 00000040B999 0 ,-./012245f789:
000000003DAB 00000040B9AB 0 >_@JB/@
000000003DB5 00000040B9B5 0 HIJKLMNOPP
000000003DD9 00000040B9D9 0 lmnopqrstt
000000003DE4 00000040B9E4 0 wxyzv|
000000004028 00000040C028 0 Kernel32.dll
000000004041 00000040C041 0 LoadLibraryA
00000000404F 00000040C04F 0 GetProcAddress
0000000040B9 00000040C0B9 0 .>GVm
000000004414 00000040C414 0 VRwqB
000000004847 00000040C847 0 VE?rt
00000000488F 00000040C88F 0 x<TF{
000000004918 00000040C918 0 c&(mM
000000004AEB 00000040CAEB 0 aAhBb
000000004B0C 00000040CB0C 0 N#%Z:
000000004B4B 00000040CB4B 0 ge+5jJ
000000004C14 00000040CC14 0 i-'lo
000000004DD7 00000040CDD7 0 z~JX]=$:
000000004DFC 00000040CDFC 0 yK!fF
000000004F3B 00000040CF3B 0 cxv1v
000000004F8C 00000040CF8C 0 ]#F_NDF{
000000004FF7 00000040CFF7 0 ixJ e
0000000050D3 00000040D0D3 0 pRQW\
0000000050E0 00000040D0E0 0 P_J_b
000000005316 00000040D316 0 ,p_k-b
000000005466 00000040D466 0 cn1u<
000000005476 00000040D476 0 gr5i@
000000005603 00000040D603 0 |n!#h
000000005631 00000040D631 0 s.sS6,t
000000005737 00000040D737 0 lwN%;b
000000005AA6 00000040DAA6 0 Vcf4Oj
00000000614B 00000040E14B 0 ,,,EX
00000000619F 00000040E19F 0 $*\D>e
0000000061CF 00000040E1CF 0 0FhP:q
000000006572 00000040E572 0 Ck|10
00000000660B 00000040E60B 0 abWVD
000000006744 00000040E744 0 iu-|i
00000000696E 00000040E96E 0 @k6s>
000000006C72 00000040EC72 0 fq4x?
000000006CC6 00000040ECC6 0 X\{gI
000000006E66 00000040EE66 0 2\fr5
000000006E8C 00000040EE8C 0 S_>8$P
000000007146 00000040F146 0 /R va
0000000072A4 00000040F2A4 0 du3YX
=== DOWNLOAD ===
Mirror provided by vx-underground.org, thx!
=== PEDUMP REPORT ===
=== MZ Header ===
signature: "MZ"
bytes_in_last_block: 64 0x40
blocks_in_file: 1 1
num_relocs: 0 0
header_paragraphs: 2 2
min_extra_paragraphs: 4 4
max_extra_paragraphs: 65535 0xffff
ss: 2 2
sp: 64 0x40
checksum: 0 0
ip: 14 0xe
cs: 0 0
reloc_table_offset: 28 0x1c
overlay_number: 0 0
reserved0: 3706015365755568128 0x336e695700000000
oem_id: 8242 0x2032
oem_info: 28271 0x6e6f
reserved2: 220297580 0xd21796c
reserved3: 3020825610 0xb40e240a
reserved4: 47625 0xba09
reserved5: 3089222943 0xb821cd1f
reserved6: 567102465 0x21cd4c01
lfanew: 64 0x40
=== DOS STUB ===
00000000: 57 69 6e 33 32 20 6f 6e 6c 79 21 0d 0a 24 0e b4 |Win32 only!..$..|
00000010: 09 ba 00 00 1f cd 21 b8 01 4c cd 21 40 00 00 00 |......!..L.!@...|
=== PE Header ===
signature: "PE\x00\x00"
# IMAGE_FILE_HEADER:
Machine: 332 0x14c x86
NumberOfSections: 10 0xa
TimeDateStamp: "2026-01-14 09:44:18"
PointerToSymbolTable: 0 0
NumberOfSymbols: 0 0
SizeOfOptionalHeader: 224 0xe0
Characteristics: 783 0x30f RELOCS_STRIPPED, EXECUTABLE_IMAGE
LINE_NUMS_STRIPPED, LOCAL_SYMS_STRIPPED
32BIT_MACHINE, DEBUG_STRIPPED
# IMAGE_OPTIONAL_HEADER32:
Magic: 267 0x10b 32-bit executable
LinkerVersion: 2.24
SizeOfCode: 8192 0x2000
SizeOfInitializedData: 20992 0x5200
SizeOfUninitializedData: 512 0x200
AddressOfEntryPoint: 50505 0xc549
BaseOfCode: 4096 0x1000
BaseOfData: 12288 0x3000
ImageBase: 4194304 0x400000
SectionAlignment: 4096 0x1000
FileAlignment: 512 0x200
OperatingSystemVersion: 4.0
ImageVersion: 1.0
SubsystemVersion: 4.0
Reserved1: 0 0
SizeOfImage: 86016 0x15000
SizeOfHeaders: 1024 0x400
CheckSum: 67975 0x10987
Subsystem: 2 2 WINDOWS_GUI
DllCharacteristics: 0 0
SizeOfStackReserve: 2097152 0x200000
SizeOfStackCommit: 4096 0x1000
SizeOfHeapReserve: 1048576 0x100000
SizeOfHeapCommit: 4096 0x1000
LoaderFlags: 0 0
NumberOfRvaAndSizes: 16 0x10
=== DATA DIRECTORY ===
EXPORT rva:0x 0 size:0x 0
IMPORT rva:0x c000 size:0x 60
RESOURCE rva:0x a000 size:0x 1a18
EXCEPTION rva:0x 0 size:0x 0
SECURITY rva:0x 0 size:0x 0
BASERELOC rva:0x 0 size:0x 0
DEBUG rva:0x 0 size:0x 0
ARCHITECTURE rva:0x 0 size:0x 0
GLOBALPTR rva:0x 0 size:0x 0
TLS rva:0x f6d9 size:0x 18
LOAD_CONFIG rva:0x 0 size:0x 0
Bound_IAT rva:0x 0 size:0x 0
IAT rva:0x 0 size:0x 0
Delay_IAT rva:0x 0 size:0x 0
CLR_Header rva:0x 0 size:0x 0
rva:0x 0 size:0x 0
=== SECTIONS ===
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
1000 2000 1000 400 0 0 0 0 c0000040 RW- IDATA
3000 1000 200 1400 0 0 0 0 c0000040 RW- IDATA
4000 1000 200 1600 0 0 0 0 c0000040 RW- IDATA
5000 1000 400 1800 0 0 0 0 c0000040 RW- IDATA
6000 1000 0 1c00 0 0 0 0 c0000040 RW- IDATA
7000 1000 400 1c00 0 0 0 0 c0000040 RW- IDATA
8000 1000 200 2000 0 0 0 0 c0000040 RW- IDATA
9000 1000 200 2200 0 0 0 0 c0000040 RW- IDATA
.rsrc a000 2000 1c00 2400 0 0 0 0 c0000040 RW- IDATA
.UPX c000 9000 3800 4000 0 0 0 0 c0000040 RW- IDATA
=== TLS ===
RAW_START RAW_END INDEX CALLBKS ZEROFILL FLAGS
409001 40901c 414000 408004 0 0
=== RESOURCES ===
FILE_OFFSET CP LANG SIZE TYPE NAME
0x24e8 0 0 5672 ICON #1
0x3b10 0 0 754 DIALOG #100
0x3e04 0 0 20 GROUP_ICON #102
[?] can't find file_offset of VA 0x14000
=== IMPORTS ===
MODULE_NAME HINT ORD FUNCTION_NAME
Kernel32.dll 0 LoadLibraryA
Kernel32.dll 0 GetProcAddress
=== Packer / Compiler ===
yoda's Protector v1.03.2(.dll,.ocx) (Ashkbiz Danehkar)
=== Strings ===
File pos Mem pos ID Text
======== ======= == ====
000000000020 000000400020 0 Win32 only!
000000000278 000000400278 0 .rsrc
0000000004BE 0000004010BE 0 htc>n
0000000005FB 0000004011FB 0 a<&MRuZ
0000000006DF 0000004012DF 0 >w.*e
0000000006E6 0000004012E6 0 u/d\A
000000000985 000000401585 0 %v(=*"
0000000009E5 0000004015E5 0 \_MG_
000000000B19 000000401719 0 Gf.6xs6P
000000000B39 000000401739 0 >gY+m[qq,)7u
000000000BFA 0000004017FA 0 f,]8B
000000000C43 000000401843 0 DOLKG
000000000D85 000000401985 0 V\~ET
000000000DE0 0000004019E0 0 RZ~P)
000000000E41 000000401A41 0 R<~/J
000000000EA7 000000401AA7 0 KpZ5+
000000000F95 000000401B95 0 ~R[tN*
00000000120C 000000401E0C 0 &53qW
0000000013EE 000000401FEE 0 b~+*es
00000000158B 00000040318B 0 ],I*:
0000000017B6 0000004041B6 0 V7pThl\
000000001D1E 00000040711E 0 hUL 0'
000000001D93 000000407193 0 ,_{bM
000000001ECA 0000004072CA 0 .RvT]MM
000000001FF8 0000004073F8 0 FUtAM
00000000293D 00000040A53D 0 &&&&&&&&&
0000000029A5 00000040A5A5 0 QQQQQ
0000000029BB 00000040A5BB 0 &&&&&&&&&
0000000029DA 00000040A5DA 0 ?????????QQQQ
0000000029FA 00000040A5FA 0 QQQ?????????
000000002A23 00000040A623 0 NNNNN:::::::::::::::::::::NNN
000000002A59 00000040A659 0 [[[[[
000000002BC1 00000040A7C1 0 =======
000000002C10 00000040A810 0 QQQ :
000000002C50 00000040A850 0 QQ? :
000000002C90 00000040A890 0 QQ? :\
00000000309A 00000040AC9A 0 ]]]]]]]]
0000000030AC 00000040ACAC 0 ]]]]]]]]]
0000000030EB 00000040ACEB 0 LL_____
0000000030F3 00000040ACF3 0 LLLLX
0000000030FC 00000040ACFC 0 VXXXLXXXXXXXV
00000000322B 00000040AE2B 0 '''''''''''''
00000000325A 00000040AE5A 0 YYY::Y:NNNNddcccd
000000003428 00000040B028 0 #N#ff
0000000035A0 00000040B1A0 0 N*++BBB*
000000003615 00000040B215 0 iNi##
0000000036A2 00000040B2A2 0 :bgbf
0000000036B1 00000040B2B1 0 iAcfb
0000000036E6 00000040B2E6 0 & Q#
000000003723 00000040B323 0 bAp88(
000000003754 00000040B354 0 Ncdc:N
000000003823 00000040B423 0 &&&&&
00000000387F 00000040B47F 0
000000003B8D 00000040B78D 0 !"I$'&P(M*+,
000000003B9D 00000040B79D 0 0C23456489j;<=>x@@BlDhFGH
000000003BBB 00000040B7BB 0 NOPQRPTU
000000003BCF 00000040B7CF 0 bcd:;
000000003BD5 00000040B7D5 0 hujklmnlpq
000000003BE0 00000040B7E0 0 stuvvx
000000003BEB 00000040B7EB 0 ~j|VW
File pos Mem pos ID Text
======== ======= == ====
000000003C8C 00000040B88C 0 e !"#$%&'((b+,-.d042O4/684
000000003CA9 00000040B8A9 0 <n>o@
000000003CB1 00000040B8B1 0 DEFGHIJKLL
000000003CC1 00000040B8C1 0 TXVsXSZWX23
000000003CD5 00000040B8D5 0 hijklmnnpq
000000003CE0 00000040B8E0 0 stuvtx
000000003CEB 00000040B8EB 0 ~||VW
000000003D8D 00000040B98D 0 9"C$.&1$
000000003D99 00000040B999 0 ,-./012245f789:
000000003DAB 00000040B9AB 0 >_@JB/@
000000003DB5 00000040B9B5 0 HIJKLMNOPP
000000003DD9 00000040B9D9 0 lmnopqrstt
000000003DE4 00000040B9E4 0 wxyzv|
000000004028 00000040C028 0 Kernel32.dll
000000004041 00000040C041 0 LoadLibraryA
00000000404F 00000040C04F 0 GetProcAddress
0000000040B9 00000040C0B9 0 .>GVm
000000004414 00000040C414 0 VRwqB
000000004847 00000040C847 0 VE?rt
00000000488F 00000040C88F 0 x<TF{
000000004918 00000040C918 0 c&(mM
000000004AEB 00000040CAEB 0 aAhBb
000000004B0C 00000040CB0C 0 N#%Z:
000000004B4B 00000040CB4B 0 ge+5jJ
000000004C14 00000040CC14 0 i-'lo
000000004DD7 00000040CDD7 0 z~JX]=$:
000000004DFC 00000040CDFC 0 yK!fF
000000004F3B 00000040CF3B 0 cxv1v
000000004F8C 00000040CF8C 0 ]#F_NDF{
000000004FF7 00000040CFF7 0 ixJ e
0000000050D3 00000040D0D3 0 pRQW\
0000000050E0 00000040D0E0 0 P_J_b
000000005316 00000040D316 0 ,p_k-b
000000005466 00000040D466 0 cn1u<
000000005476 00000040D476 0 gr5i@
000000005603 00000040D603 0 |n!#h
000000005631 00000040D631 0 s.sS6,t
000000005737 00000040D737 0 lwN%;b
000000005AA6 00000040DAA6 0 Vcf4Oj
00000000614B 00000040E14B 0 ,,,EX
00000000619F 00000040E19F 0 $*\D>e
0000000061CF 00000040E1CF 0 0FhP:q
000000006572 00000040E572 0 Ck|10
00000000660B 00000040E60B 0 abWVD
000000006744 00000040E744 0 iu-|i
00000000696E 00000040E96E 0 @k6s>
000000006C72 00000040EC72 0 fq4x?
000000006CC6 00000040ECC6 0 X\{gI
000000006E66 00000040EE66 0 2\fr5
000000006E8C 00000040EE8C 0 S_>8$P
000000007146 00000040F146 0 /R va
0000000072A4 00000040F2A4 0 du3YX
000000000020 000000400020 0 Win32 only!
000000000278 000000400278 0 .rsrc
0000000004BE 0000004010BE 0 htc>n
0000000005FB 0000004011FB 0 a<&MRuZ
0000000006DF 0000004012DF 0 >w.*e
0000000006E6 0000004012E6 0 u/d\A
000000000985 000000401585 0 %v(=*"
0000000009E5 0000004015E5 0 \_MG_
File pos Mem pos ID Text
======== ======= == ====
000000000B19 000000401719 0 Gf.6xs6P
000000000B39 000000401739 0 >gY+m[qq,)7u
000000000BFA 0000004017FA 0 f,]8B
000000000C43 000000401843 0 DOLKG
000000000D85 000000401985 0 V\~ET
000000000DE0 0000004019E0 0 RZ~P)
000000000E41 000000401A41 0 R<~/J
000000000EA7 000000401AA7 0 KpZ5+
000000000F95 000000401B95 0 ~R[tN*
00000000120C 000000401E0C 0 &53qW
0000000013EE 000000401FEE 0 b~+*es
00000000158B 00000040318B 0 ],I*:
0000000017B6 0000004041B6 0 V7pThl\
000000001D1E 00000040711E 0 hUL 0'
000000001D93 000000407193 0 ,_{bM
000000001ECA 0000004072CA 0 .RvT]MM
000000001FF8 0000004073F8 0 FUtAM
00000000293D 00000040A53D 0 &&&&&&&&&
0000000029A5 00000040A5A5 0 QQQQQ
0000000029BB 00000040A5BB 0 &&&&&&&&&
0000000029DA 00000040A5DA 0 ?????????QQQQ
0000000029FA 00000040A5FA 0 QQQ?????????
000000002A23 00000040A623 0 NNNNN:::::::::::::::::::::NNN
000000002A59 00000040A659 0 [[[[[
000000002BC1 00000040A7C1 0 =======
000000002C10 00000040A810 0 QQQ :
000000002C50 00000040A850 0 QQ? :
000000002C90 00000040A890 0 QQ? :\
00000000309A 00000040AC9A 0 ]]]]]]]]
0000000030AC 00000040ACAC 0 ]]]]]]]]]
0000000030EB 00000040ACEB 0 LL_____
0000000030F3 00000040ACF3 0 LLLLX
0000000030FC 00000040ACFC 0 VXXXLXXXXXXXV
00000000322B 00000040AE2B 0 '''''''''''''
00000000325A 00000040AE5A 0 YYY::Y:NNNNddcccd
000000003428 00000040B028 0 #N#ff
0000000035A0 00000040B1A0 0 N*++BBB*
000000003615 00000040B215 0 iNi##
0000000036A2 00000040B2A2 0 :bgbf
0000000036B1 00000040B2B1 0 iAcfb
0000000036E6 00000040B2E6 0 & Q#
000000003723 00000040B323 0 bAp88(
000000003754 00000040B354 0 Ncdc:N
000000003823 00000040B423 0 &&&&&
00000000387F 00000040B47F 0
000000003B8D 00000040B78D 0 !"I$'&P(M*+,
000000003B9D 00000040B79D 0 0C23456489j;<=>x@@BlDhFGH
000000003BBB 00000040B7BB 0 NOPQRPTU
000000003BCF 00000040B7CF 0 bcd:;
000000003BD5 00000040B7D5 0 hujklmnlpq
000000003BE0 00000040B7E0 0 stuvvx
000000003BEB 00000040B7EB 0 ~j|VW
000000003C8C 00000040B88C 0 e !"#$%&'((b+,-.d042O4/684
000000003CA9 00000040B8A9 0 <n>o@
000000003CB1 00000040B8B1 0 DEFGHIJKLL
000000003CC1 00000040B8C1 0 TXVsXSZWX23
000000003CD5 00000040B8D5 0 hijklmnnpq
000000003CE0 00000040B8E0 0 stuvtx
000000003CEB 00000040B8EB 0 ~||VW
000000003D8D 00000040B98D 0 9"C$.&1$
File pos Mem pos ID Text
======== ======= == ====
000000003D99 00000040B999 0 ,-./012245f789:
000000003DAB 00000040B9AB 0 >_@JB/@
000000003DB5 00000040B9B5 0 HIJKLMNOPP
000000003DD9 00000040B9D9 0 lmnopqrstt
000000003DE4 00000040B9E4 0 wxyzv|
000000004028 00000040C028 0 Kernel32.dll
000000004041 00000040C041 0 LoadLibraryA
00000000404F 00000040C04F 0 GetProcAddress
0000000040B9 00000040C0B9 0 .>GVm
000000004414 00000040C414 0 VRwqB
000000004847 00000040C847 0 VE?rt
00000000488F 00000040C88F 0 x<TF{
000000004918 00000040C918 0 c&(mM
000000004AEB 00000040CAEB 0 aAhBb
000000004B0C 00000040CB0C 0 N#%Z:
000000004B4B 00000040CB4B 0 ge+5jJ
000000004C14 00000040CC14 0 i-'lo
000000004DD7 00000040CDD7 0 z~JX]=$:
000000004DFC 00000040CDFC 0 yK!fF
000000004F3B 00000040CF3B 0 cxv1v
000000004F8C 00000040CF8C 0 ]#F_NDF{
000000004FF7 00000040CFF7 0 ixJ e
0000000050D3 00000040D0D3 0 pRQW\
0000000050E0 00000040D0E0 0 P_J_b
000000005316 00000040D316 0 ,p_k-b
000000005466 00000040D466 0 cn1u<
000000005476 00000040D476 0 gr5i@
000000005603 00000040D603 0 |n!#h
000000005631 00000040D631 0 s.sS6,t
000000005737 00000040D737 0 lwN%;b
000000005AA6 00000040DAA6 0 Vcf4Oj
00000000614B 00000040E14B 0 ,,,EX
00000000619F 00000040E19F 0 $*\D>e
0000000061CF 00000040E1CF 0 0FhP:q
000000006572 00000040E572 0 Ck|10
00000000660B 00000040E60B 0 abWVD
000000006744 00000040E744 0 iu-|i
00000000696E 00000040E96E 0 @k6s>
000000006C72 00000040EC72 0 fq4x?
000000006CC6 00000040ECC6 0 X\{gI
000000006E66 00000040EE66 0 2\fr5
000000006E8C 00000040EE8C 0 S_>8$P
000000007146 00000040F146 0 /R va
0000000072A4 00000040F2A4 0 du3YX
=== DOWNLOAD ===
Mirror provided by vx-underground.org, thx!